What Makes A Good Password?
As more and more of our lives move online, we end up accumulating more and more accounts each of which has its own password. It feels like almost every site has its own policy, ranging from lax to inane. But, is 4$%nT;6**a really safer than Butterfly5Cat5WaffleIron? What really makes a good password?
A good password is a product of its entropy, which is affected by the complexity and length of the password. Password reuse reduces or even eliminates security. How do these things work together and what does 2FA do to the equation? Let’s also see how to make some easy to remember passwords.
Entropy
A password’s strength is governed by its bits of entropy. Each bit of entropy is equivalent to an exponential growth in possibilities for the password. What this boils down to is that the longer a password is, the more limited the set of characters used can be (within reason) without necessarily harming the security. The complexity and length each play a part and serve as dimension for security. We’ll hit the math in a bit.
Entropy is powerful because it gives you a way to tell how much more difficult a password is in a more digestable format, but it has its limitations. It is not a panacea to security. Password1! is not as real world secure as Meyapar or similar gibberish. A hacker can make certain assumptions in order to reduce the bits of entropy they test, and potentially succeed. Passwords security means nothing if the database is breached. You buy time with hashes.
Some companies still employ systems which employ plain-text passwords. This renders your password compromised the second the company is breached. A legacy version of Ruby on Rails, or any number of platforms mean that your password may be ripe for the taking. There’s far more than entropy to contend with in the real world.
Password Complexity and Length
The traditional view of password security was that the more complex the better, though this is just one small part of the picture. The length plays in as much as the complexity. An extremely complex password which is short is as bad as an extremely simple password which is longer. When you look at complexity, you also need to take into account several variables to determine how many practical bits of entropy you have.
A mixed case only password will have 52 possible characters, an alphanumeric password will have 62. You can begin to add more characters to get every ASCII character or go even further with Unicode. Some sites have a minimum length, and others have a maximum. The way to approach the balance is to look at the possibilities mathematically.
If we look at raw possibilities, we get that potential charactersnumber of characters will define our number of password possibilities. This is only the number of possibilities though, and not really a true measure of security yet. Possibilities can be reduced with either the right knowledge or the right gamble.
While a password composed of 2 words from a 40,000 word dictionary could be dozens of characters long easily (with 40,0002 = 4e+08), it is about on par with a 6 character alphanumeric password in the grander scheme of things (526 = 9e+08). All it takes is the attacker knowing, or guessing that your password is composed a certain way to more easily compromise it. Or, they can compromise the admin account for your service and have a take at the hashes.
Reusing Passwords
We all have a million accounts and it gets frustrating accounting for every password. While there are solutions which help with remembering passwords, they can be annoying. Sometimes you need to setup a password and don’t get the chance (or forget) to put it in your device. Other times, you just want to use the service.
Many people reuse passwords. It’s unfortunate, but it’s true. Reuse of a password compromises it in a way which bits of entropy can’t account for. How does the service store your password, and how many other services do you use which have the same username (or close enough), and the same password?
It’s fine to reuse passwords for burner services which have no bearing on your life, but once you reuse with a bank or similar, you run the risk of being fully compromised. Many people also forget to reset passwords after a breach, or they don’t even know it happened. There have been countless breaches in the past decade, how many have impacted you and how many do you know about?
Multi-Factor Authentication
Multi-factor authentication (MFA) is a technique to add an algorithmically generated password to logins. The logic goes that by adding a secondary password which is impossible to forget (though it can be lost), you can clamp down after fewer attempts. This means that a password with okay entropy might lead to a low entropy password which locks after 10 failed attempts and alerts the user.
This is the compromise security has made which ends up being substantially more secure. Since the code is random and cycles constantly, it is going to be near impossible to crack barring chance or a broken algorithm. Though there is the risk that some 2FA algorithms might be predictable, they are predicated on a secret key which shouldn’t be exposed. If you crack this far up the chain, you’ve cracked more than encryption can do anything about.
You have to have some degree of trust somewhere in the chain, and you have to assume that a physical and knowledge requirement should be enough for all but the most dedicated hackers. Where do you trade off practicality for security, and how do you stop your user from just writing the password down on their list on their computer? That 100 character requirement is now useless to stop anyone who walks in front of that computer.
What Holes Exist with MFA?
MFA at least ensures that the hacker needs the password and the phone or similar device. Users can still install an authenticator on their computer and write down the password, but you have taken as much care as you can. You can’t stop them, but now their security is entirely on them.
Your car may not drive with you buckled up, but you can always cut the belt and plug it in. If the belt has smart technology and similar, it’s still possible, but it’s probably just angering customers. Where does your responsibility end? You already implied your “do not drink” warning on the security bleach, why would you try and design a drink-proof bottle which will just enrage the other 99.99% of your customers who aren’t actively working against themselves?
MFA also doesn’t stop certain combined attacks. If someone is out to get you by stealing access to your phone and compromise multiple passwords (account password and phone keycode), they’re operating above the pay grade of your password solution. The attacker will just target the service instead, or use rubber hose cryptography at worst. You’re usually dealing with a movie scenario rather than reality at this point.
How This All Works Together
The complexity and length both make a password have higher bits of potential entropy, but predictable factors reduce those bits of entropy. If you’re using a long alphanumeric password, and it’s 2 words from a 40,000 word dictionary, you haven’t accomplished as much as you think you have from the math. This reduction does depend on the attacker knowing or at least gambling on the possibility.
This possibility of compromise gets higher as they target the system itself which means you should avoid reusing passwords, especially with similar usernames. You’re looking at 1 bit of entropy if the credentials are identical. MFA and 2FA can reduce this substantially, to the point you only really have to worry about this with spy film plot level events. They do happen, but most hackers just hit a different route.
The more unpredictability you can add into each password, the more likely you are to approach the higher end of the number of possibilities a computer has to go through. 00000000aA! is going to be cracked quicker on a system which iterates through each possibility with numbers at the start, the alphabet next, then symbols. While the password crackers I used back in the day used this method, newer ones use its evolution (if you want to take the gamble).
Crafting a Password
What are the known bits of entropy if they know what you did and what are the bits of entropy if they don’t? You want a balance without going too crazy. I like to use non-dictionary words with numbers and symbols to make easy to remember passwords.
A jumble of numbers, letters, and symbols is a pain, but something like $Tokyo7sutra%REVERE!!! is going to be much, much easier. While this password is easy to remember on its own, how do you keep track of it? I like to use something like a password algorithm to generate more complex passwords where possible. This doesn’t work for every account, but it helps cut down on a lot of them. You can always use a password app to circumvent this, but it’s good to have on hand.
To generate a secure password, you need to increase the complexity and length to raise the bits of entropy. You also need to take into account how many bits of entropy exist if someone gambles on guessing parts of your password. Your strategy can be as simple as a prefix and a suffix or a mix of affixes and interspersed characters. Mix in rules for casing and similar which are predictable, to you, and you can further increase the complexity.
Password Algorithms
If you use the password Password, you’re looking at virtually no bits of entropy from a modern dictionary based brute-force program. If you use this as a prefix and intersperse symbols, you greatly raise the complexity without making it harder for yourself. Password@google is substantially more secure but it also isn’t that easy if you don’t know the process. You can throw in a number at the beginning, the middle somewhere, or the end and make it even more difficult to guess. The bits of entropy won’t go up that much for knowing the algorithm though. How likely is your algorithm to be common enough to have rules for it?
The more arbitrary rules you use, the harder it will be for more dedicated hackers to see the pattern. At a certain point though, if you’re a target, you’ll need far more than a password to stay secure. Though quantum computing puts forward the promise to break modern cryptography, we still have a good while before it works out the details enough to actually do it. You’re far more likely to be compromised by social engineering, malware, a breach to the service itself, phishing, a break in the cryptography algorithm, etc. than a smash and grab password hack if you use a non-trivial, secure password.
Use an algorithm which is diverse enough that even knowing the basic rules isn’t enough to trivially compromise it. Have rules to make it easy to adjust and remember the password despite required changes. Split up services and use easier passwords for less important services and harder passwords for more important ones if nothing else. Make your financial sites each unique and don’t worry about some forum you got for a download and some site you signed up for coupons at. What the site contains affects how much security really needs to matter.

by Sage Driskell
Common Phishing Techniques
“Microsoft Support” | This is an extremely common scheme that many people fall for. Someone receives a call or email from “Microsoft” saying they’re compromised, and the “technician” helps the user allow them to connect to the machine in order to compromise their system. A lot of times, they leave behind malware or other remote access tools which they can use to later harvest information. They also typically charge for their “assistance” and collect data either via an invoice or on the phone.
Bank Emails | This is the most well-known phishing attempt. You get an email “from your financial institution” and the domain is usually close to the original, but always a bit suspect. These pages are identical to the bank’s page as well. The easiest way to avoid these is to always log in to the bank site directly rather than doing anything from an unknown communication from them unless you specifically know an email is coming (e.g. password reset).
IRS Emails | As we know, the IRS is almost impossible to work with, so they won’t make your life easy to just call you and square everything away over the phone or via email. These types of phishing attempts typically involve “the IRS” reaching out to you about a “tax issue” and they’re glad to either collect information (including your social) to “process your case”, or in some cases, they’ll take money to help “pay off the owed sum today only”.
Compromised Service Emails | These are a “warning” from a provider that “the service may have been compromised” and they need your details to continue. The login page is usually either really good or else really obviously bad. There is very rarely a middle ground on these. They will sometimes include a specific email or form to make it easier.
Fake Invoices | This is a fake invoice requesting money for some service. These are commonly used to target companies. The invoices are usually extremely generic, may or may not ask for personal details, and target companies where it is easy to miss a small expense.
419 Scam | These used to just be scams, but they’ve grown in some ways. The goal is to get both your money and your identity. These will typically be a business venture or something, but unlike classic 419 scams, they don’t just start asking for $10k for your $10mil “which is stuck in processing and needs the money to be released, Western Union only please!” These will start out as small investment opportunities or similar which may actually show some signs of legitimacy before the big hit.
Spear Phishing | You know that cool flash drive or CD you found in the parking lot near your sensitive workplace? It may be infected with malware or spyware to try and infiltrate your environment. That is the most common spear phishing technique at present. It’s literally just a cool looking piece of media loaded with all sorts of malware.
Signs It’s a Phishing Email
The first thing to look for in any questionable email is this: is this someone I do business with? If you don’t have an account, you obviously have no business receiving their email except as spam. Another thing to look for is the trends of the institution. What I mean by this is, if you’re dealing with a bank, they don’t want you to email them a form. Look for obvious grammar and spelling mistakes. These can be telltale sign that something is amiss. Most financial institutions and similarly private types of institutions want you to sign in and fill it out on their page and will almost always have an internal way to do this from their login from an internal messaging portal or similar. If in doubt, log in directly and look and see if this is a legitimate communication. If it is, you may still be compromised and should still take caution.
Another thing to look at is the domain. Does the domain match the exact one you use for your bank or similar? The names may be very close, but they tend to have some minor issue with them or will redirect through something else. Just because it looks right doesn’t mean it is. You can also check the SSL certificate to see if it is legitimate or not, but that’s a bit more complicated.
Any service which is reaching out can also be called or otherwise contacted to verify the legitimacy of a claim. No one has time for every communication, but anything which looks pressing may be worth trying to communicate with the vendor or service over. I personally just ignore everything unless I get officially contacted about it or know it’s coming.
Another strategy I use is different email accounts tied to specific services. I work with one bank with one account and another bank with a different account. I know I can only receive one banks communication on a specific email, so anything on the other email is obviously a trick. Using email accounts only for specific accounts (and literally nothing else) helps well since you have a lower chance of the email being leaked, but this does require more effort and upkeep.
Further Signs
For more advanced users, you can look at the email headers (to do this in Outlook, see: https://www.technipages.com/outlook-view-message-headers). If you see something like the following message:
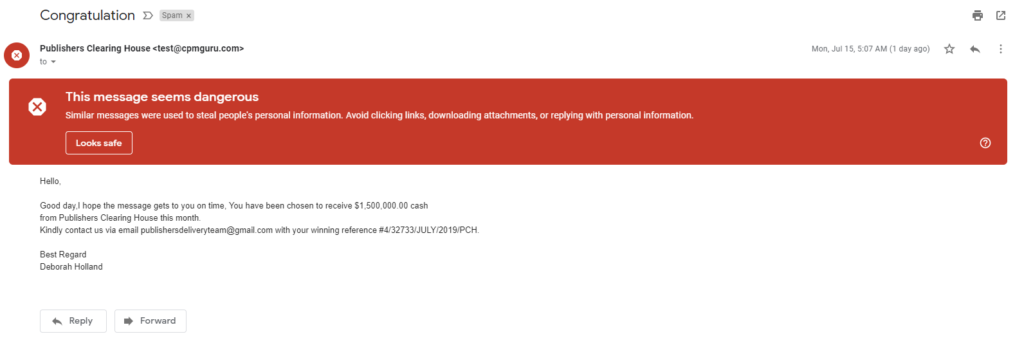
We can see that this is coming from a [email protected] — which I have no idea what that is — and the email to contact is [email protected]. The domains do not match and neither of these have anything to do with Publisher’s Clearing House. I could not find a specific phishing email in my mailbox with forged headers, but see something like: https://www.alienvault.com/blogs/security-essentials/how-hackers-manipulate-email-to-defraud-you-and-your-customers for an example of what to look for. There are legitimate uses for a “forged” header, but this is typically for bulk mailers and similar, and is rare with official communication.
Another thing to look at is the TLD. If the TLD is foreign for something which is US only, you can almost guarantee the email is a phishing attempt. If the TLD doesn’t match the actual company TLD, then you probably have an issue too. Apple.net is not Apple.com. Tech giants like Apple will tend to nail down sister domains, but smaller companies usually don’t have the resources to do this.
Another trick is to copy and paste the domain from the email into something like: https://www.diffchecker.com/ and then copy the domain from the email. You might get something like:
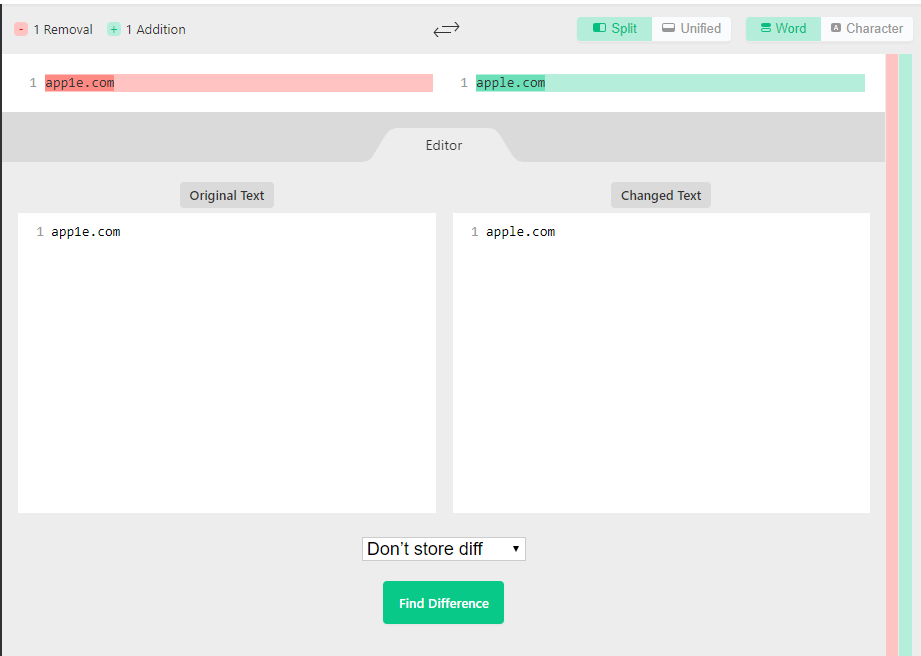
This is obviously a phishing attempt since the domains do not match. With the right font, these are somewhat obvious, but a common tactic is to use Unicode characters or similar characters in another language in order to get around this sort of limitation. This technique helps weed out some of the more obvious tricks, but you should still check the headers.
How The 20’s Security Offerings Mitigate Phishing
Vipre Email Security
Vipre Email Security is the new name for Fusemail. This service blocks both malware and phishing at the source. You don’t need to worry about a user clicking on malware or getting phished if they don’t even see it in the first place. Setup is easy and convenient and is pretty much ready to go (that is, no crazy lists or other hoops like some services) once the initial setup is complete. No solution is perfect however, so training and combination with a tool like OpenDNS makes this tool substantially more powerful. Vipre Email Security gives you the control to throttle scams and phishing attempts in order to keep your clients safe.
OpenDNS
OpenDNS isn’t typically thought of as a way to mitigate phishing attempts, but it works great against fake portals. OpenDNS is easily configurable and scalable for agents at your client’s sites. It prevents the few phishing attempts which get by from being as impactful. There are caveats to this however, but we have seen many tickets from confused users unable to submit their sensitive data to scammers. OpenDNS is flexible and easy to deploy to individual agents or across a network. From a domain environment to workers in the field, OpenDNS has an option to get you covered.
Deep Instinct and Huntress
Deep Instinct and Huntress help prevent and remove compromises from the inside which can lead to legitimate emails becoming weaponized into near impossible to discern phishing from legitimate accounts. By preventing infections, you prevent data leakage and lock down on threats which may threaten your client’s systems with ransomware as well as keyloggers. Deep Instinct and Huntress are like Yin and Yang. Deep Instinct is the prevention, Huntress is the remediation. Find exploits on new clients and help lock them down preventing more seemingly legitimate, internal threats which lead to phishing and worse.
To learn more about The 20 and how we can help your business, be sure to check us out here!

by Sage Driskell
MSPs large and small are systematically being targeted over and over in the news. It’s almost weekly a new article comes out about a given large provider being targeted. Many of these attacks come from API weaknesses. You can’t control the provider or service, but you can minimize the chance of these attacks impacting you and your customers.
Leaky APIs
Leaky APIs are APIs which allow easy exfiltration of data from a service. These exploits often stem from deprecated APIs or privilege escalations. Many deprecated APIs exist in products for backwards compatibility, but they often come with caveats and holes.
Privilege escalations can happen on APIs due to loose queries which can return data from outside of their scope. Other escalations rely on multiple APIs which accidentally return data outside the scope a user can see normally due to their interactions. A deprecated API may help break another API when glued together with the wrong product.
These types of attacks are often used to harvest credentials or information for attacks later. Stolen passwords can be used on any similar account on multiple platforms to see what is shared. Hackers glean data which makes their later attacks easier either for traditional attacks or for things like phishing attacks.
Weaponizing APIs
With the creation of things like fileless malware and easy, privileged access via RMM tools, weaponizing an API has never been easier. Other products like Webroot have been had similar incidents from adding the feature to run commands remotely. This feature creep combined with API access makes these tools further targets.
Most products rely on various SQL products for databases. Many APIs where the developers are not security conscious will be a thin layer between the user and raw SQL queries. These can be weaponized to poison the data allowing greater access or to exfiltrate useful data. Depending on the product, it may be possible to insert hostile, arbitrary code which gets run by something within the API. Some RMMs even store scripts as blobs in the database.
How Do These Attacks Happen?
These attacks happen because of lax security policies on both sides of the equation. Many vendors do not take into account the ramifications of the access their API can provide. Vendors which integrate their products may ask for more permissions than they should need to function. A lot of permission sets are too permissive in general because its easier for the developer and the user to set up.
Clients of these products often fail to limit users enough. API users floating around provide an easy in to a company if they are compromised. Sometimes, the way multiple APIs talk to one another may be targeted as well. A simple return status from a query in a limited API may provide information that the other API would not normally have given. A simple boolean reply may provide a necessary bit of information for a malicious actor to work off of.
What Can You Do?
Removing unnecessary API users or users which may have API access is one of the easiest steps to protecting yourself, even from APIs outside of your control. Turning obsolete or unnecessary API versions, or even entire APIs off, is another great step. Use it or lose it. Trim off enough of the fat, and the hunter will target easier, more profitable prey.
Shrink your attack surface to shrink what you have to keep safe. Besides just trimming off the obsolete, scope your API users. An API user which only reports from a product doesn’t need write access. Your users need Two-Factor Authentication (2FA) everywhere possible. Do not share credentials between API users and do not recycle user names if you can help it. These basic steps have headed off many attacks before they even have the chance to become a threat with very little imposition on our technicians.
If you run products in house which have an API you use, try blocking traffic based on IP for whatever is using it. This isn’t always possible, but can often be used to limit certain service APIs to specific, known entities which limits the impact of a leaky or broken API. Rate limiting connections is another great step. If your average client hits 5 requests per hour, why not set a limit of 10 requests per hour so that brute force attempts take significantly longer? Alerting on these thresholds is another great step, especially if you control something in the stack which can see this.
Researching Products
No product is going to be perfect, but you can shop around to minimize damage. How does your current product handle exploitation? Are they quick to report it or do they take their time? A vendor which reacts fast, may still get hit, but at least you’ll know before your clients do and be able to protect yourself.
A vendor which tells you about an exploit quickly is also a vendor which works on fixing it quickly. Look at the vendor’s response history and how long it takes them to clear out serious CVEs to know how big a threat they are to your business. If they can’t keep up with serious vulnerabilities which are reported, what else are the missing that’s not reported yet?
Always be on the lookout to how a vendor impacts you and your clients. A vendor which never has real access is easier to trust than one which can make system level changes. Look out for how they handle older APIs too. A vendor which leaves deprecated features in too long runs the risk of being exploited down the line.
Ask your vendor what they do about older versions and whether or not they rate limit requests and accounts. See what the scope of their API access is. The irony is that those proudest of their APIs open access will usually be the first to tell you about it. Weigh this with your other options and the impact on your client before signing.
Our Strategy
We minimize unnecessary API interaction and work to maintain best practices to prevent exploits. When an API becomes obsolete, it is removed from our system where possible. API access is also further limited for fixed entities to prevent more wholesale access from being available off premise. Users need 2FA to get into basically anything. These patterns heavily minimize the attack surface with very little maintenance. Our large community contributes to helping make sure every potential exploit is known as soon as possible.
Our Security Focus
We focus on a holistic approach to security, and try to stay ahead of exploits and reduce the risk of any given component. Your security is only as strong as its weakest link, so you must be vigilant. Prevent unauthorized API access by preventing any access unless necessary. We want to know about an exploit as soon as it is public, if not before and be able to react to it.
Cutting off your finger is better than losing your arm, but not having to lose either is best. Prioritization of exploits is extremely important to surviving in the modern security landscape. We’re well past the days of “perfect security” even being a pipe dream, let alone realistic. We work to hedge our bets and make our platform the least ideal for hackers without sacrificing functionality. An ounce of prevention, even if it’s bitter, is a lot better than a pound of cure.
Going Forward
Stay ahead of hackers by locking down every aspect of your security. APIs are one of the most often overlooked, easily exploited part of many products. Almost every major software product is going to have an API of some kind too. Know what you’re dealing with and limit the damage where you can. MSPs have become low hanging fruit to many hackers, elevate your security and elevate yourself from being next.
Our very own Sage Driskell is a Core Services Engineer at The 20. Interested in working for us? We’re hiring!

by Monika Gupta
Remote Desktop Services (RDS) benefit employees and IT administrators alike. With employees often working from anywhere, remote desktop reduces the physical burden of carrying a work laptop home ????. It also makes updating and managing systems easier, which can alleviate the administrative burden when handling a large network. ????????
Unfortunately, a vulnerability recently discovered in RDS has the potential to let hackers remotely wreak havoc on computers or servers running RDS — and their networks — if the issue isn’t patched. Read on to learn more!
What is BlueKeep?
During Windows’ May 2019 patch cycle, Microsoft released a patch for a remote code execution bug in their Remote Desktop Services software. If left unpatched, this vulnerability could allow remote, unauthenticated attackers to execute payloads with administrative privileges and spread to other computers/servers within a network.
Errata Security CEO, Robert Graham, scanned all externally facing IP addresses on May 28th, 2019 for systems susceptible to BlueKeep… [click to continue reading]
Five Concerning Breaches That Started With an Insider Threat

by Christine Izuakor
Human beings have been dubbed as one of the most significant risks when it comes to cyber security in organizations. Behind every breach is a human or entity orchestrating an attack to make it happen. Within the affected organization, there is usually a human action that leads to the success of an insider threat attack. It could be a careless employee that clicked on a phishing email, a disgruntled employee that leaked confidential information to a competitor, or someone who wrote their username and password in a notebook that they lost while traveling. The list of events goes on and on. With so many examples, we have an opportunity to learn from all prior blunders and avoid this fate. Here are five notorious breaches that started with an insider threat.
IBM employee attempted to sell company software source code to undercover FBI agents.
A Chinese National working for IBM was one of a very select group of employees who had access to propriety software code being developed for a product. The area of the network where the company stored this information was heavily guarded. While these firewall and network security protection mechanisms could help keep unauthorized individuals out, most companies don’t build these environments expecting to have to worry about the authorized employees who are actually working on the product. In this case, IBM should have been very worried.
To financially support himself and give back to his country of origin, he quit his job, took a copy of the software code with him, and offered to sell it to China. United States officials caught wind of the Insider Threat and staged a meeting with undercover FBI agents where the Insider shared the stolen source code and even offered to edit it to remove any traces of IBM. Shortly after the meeting, he was taken into custody and eventually sentenced to five years in prison.
Understanding what people are exporting and copying from your network and having visibility into employee activity is one of many ways to prevent this type of attack.
A third party employee from a Target supplier clicks on a phishing email and impacts 70 million people in the process.
Undoubtedly one of the most talked about data breaches of the century in the security community, the Target data breach started when a third-party employee clicked on a phishing link that helped attackers get into the HVAC vendors network and eventually hop over to Target’s network. This event shed light on how it’s not just our own employees that we need to worry about, but that third parties matter as well. This was also a case where while the Insider did not have malicious intentions, this mishap from a distant Insider inflicted considerable damage to the company.
There were a host of factors that contributed to the success of this attack, but the biggest one being third-party security and account monitoring. For example, Insider Threat detection technology can provide insight into abnormal administrator accounts being created and the action taken on those accounts – activities that played a role in the success of this particular attack.
Trusted security engineer from Facebook abuses his access to stalk women online.
Cyber security professionals have a duty to protect people in the virtual world. These employees often have the most elevated access and require the most significant diligence to ensure that power is not abused. In Facebook’s case, a security engineer who dubbed himself a “professional stalker” and claimed that in his line of work he tries to “find out who hackers are in real life,” also eluded to using those same behaviors to find women in real life. This lapse of moral judgment and abuse of power added to the string of unfortunate headlines regarding security for the company, further impacting the company’s reputation amongst the user community. The engineer has since been fired.
While this may be harder to detect and prevent, correlations in activity and User Behavior Analytics may have given the company a heads up on the employee’s anomalous activities.
An insider at Punjab National Bank fraudulently gets banks to cough up $1.8 billion.
An employee at Punjab National Bank made this breach possible due to a series of gaps in security. The employee was able to organize the issuance of fake letters of understanding, a type of loan request, which prompted two banks to provide loans to PNB. The primary employee behind the Insider attack admitted to having unauthorized password access to the SWIFT system to issue these fake letters. Typically, only a select group of senior leaders in the company have access to these credentials. He also admitted to sharing that password with other users within the company, as well as staff at the third-party diamond company who orchestrated the bigger plan.
The breach shed light on the importance of governance, risk management, auditing, and the ability to cross-check system information in banking and finance. Visibility into the improper access the employee had, and the activities conducted under his login could have enabled the company to detect this earlier on.
Former Coca-Cola employee makes away with company data on a personal hard drive.
Backing up data is a standard security best practice. However, what happens when employees are copying or backing up your company information on their personal devices? Once this is done, the company has minimal visibility into the use and protection of that data, if any. This was the case when a Coca-Cola employee was separated from the company and left with personal data of 8,000 people on a personal drive. Data breach notices were issued to all of them as a result. This served as yet another reminder that companies need insight into what’s being exported and better control over data leaving their networks.
Conclusion
We can learn many lessons from these events. The most important being that Insider Threats are a considerable risk to businesses and a credible threat that companies need to take seriously. Having a robust strategy to detect, prevent and respond to Insider incidents is essential. Check out our quick guide on ways to prevent, detect and respond to an insider threat.
Christine Izuakor is the Senior Manager of Global Security Strategy and Awareness at United Airlines. Reporting directly to the CISO, she plays a critical part in embedding security in United’s culture by training the global workforce on cybersecurity, managing the organization’s security strategy and developing the teams’ talent pipeline. Izuakor earned a Ph.D. in security engineering from University of Colorado, a master’s degree in information systems security from University of Houston, is a CISSP, and serves as a grad professor at Robert Morris University. In 2017, her rapid growth within the tech industry landed her a spot on Chicago Business Crain’s Tech 50 List. Izuakor is also Co-Founder and Vice President of Gen Trend, United’s next generation business resource group.
Interested in ramping up your MSP’s cybersecurity stack? Learn more about The 20 and our newly-launched ID 20/20 User Verification Tool.
by Dr. Christine Izuakor, Contributor
Insider Threat Profiles come in many different shapes and forms and can be a frustrating problem to diagnose. Adding to the problem is the fact that even the most reliable and seemingly harmless employees can change in an instant and pose a threat. Protecting your company against these sometimes-unpredictable actors requires an understanding of the various profiles that exist and their motivations. To help, here is a quick look at five of the most common Insider Threats that companies may face, and some quick tips on how you can protect your organization from each of them.
-
Disgruntled Debbie
The disgruntled employee is often the first profile that comes to mind when most people think of Insider Threat Profiles. Disgruntled Debbie is the employee who didn’t get the performance rating or the raise she wanted and decided to retaliate. While Debbie is a fictional character, this threat is very real. For example, this became a harsh reality for Tesla one summer. An angry employee stole some of the company’s proprietary information and began to share it with 3rd parties, compromising the company’s most sensitive business assets.
-
Oblivious Oliver
Oblivious Oliver is the employee who has no clue that he is introducing risks to the organization. A large percentage of cyber security incidents start with human error, and Insider Threats are not always malicious in nature. Often, these threats stem from everyday employees who don’t know about cyber risk and, equally important, how to protect against them.
We saw a prime example of this in the RSA breach. RSA has been known as a trusted security technology provider for quite a while now, and their compromise was a stark reminder that even large security companies and their employees are not immune to attacks on the unsuspecting or oblivious employee. In this case, a simple click on a phishing email by a gullible employee led to the compromise of approximately 40 million records. The phishing attacks, like most today, were targeted and mimicked trusted contacts.
Curious employees also fall into this category. These are the employees who just want to know “What could happen if..?”, “How far might I be able to get with accessing something I shouldn’t have access to?”, “What might actually happen if I clicked on this suspicious email?”. Deep down inside, some employees are just curious kids inside, wondering what the button does.
The best solution for Oblivious Olivers is training and awareness. By helping Oliver understand the risks of clicking on malicious links and encouraging him to approach all emails with caution, attempted phishing attacks against the Oblivious Olivers of this world are less likely to succeed.
-
3rdParty Patrick
Someone doesn’t have to be a full-time employee in your organization to be considered an Insider Threat. Third party contractors and vendors often have the same or very similar access privileges even though they aren’t directly employed by the company. Their introduction of risks to the company can be intentionally or unintentionally malicious depending on the circumstance.
The list of breaches stemming from third-party errors is unending. A few examples from last year alone include Saks Fifth Ave, Lord and Taylor, Best Buy, Kmart, Delta, Target, Sears, My Fitness Pal, and many, many more. In each of these cases, the company realized significant losses as a result of their partner’s actions, or lack thereof. This makes having a strong third-party security program that includes both technology controls and legal controls against a third-party breach imperative to stopping 3rd Party Patrick dead in his tracks.
-
Terminated Tony
Noticing activity from the account of someone who’s been recently terminated? As Terminated Tony leaves, he creates back doors and tries to retain access to systems and data for future use. This is an unfortunate and costly mishap that occurs quite frequently. In one real world example, an ex-employee of Allen & Hoshall continued to access the companies files for two years after he left the company. He was able to export intellectual property worth almost half a million dollars – an action that landed him in jail for a year and a half.
Ensuring that after an employee is terminated, access to systems throughout the company and network are promptly terminated is an important step to ensuring that Terminated Tony doesn’t wreak havoc on your company after he’s gone.
-
Malicious Marvin
Unfortunately, some insiders are just downright criminals. Driven by financial hardship, gambling problems, greed, substance abuse and more – employees steal from their employers for numerous reasons. These employees are deliberately looking to breach the company’s security and take advantage. One example of this occurred when an employee from Anthem Health caused a breach that resulted in unauthorized disclosure of personal data for 18,000 patients. The file, which contained social security numbers, full names, medical information and more, was sent to the employee’s personal email address for access outside of work. It appears that the employee was intentionally stealing and misusing the data, and after the discovery of the breach, was investigated for numerous counts of suspicious activity.
Malicious Marvin is a very real threat. Life happens, and unfortunately, even the best employees make poor choices. It’s important to apply the concept of least privileged access and only grant access to users on a need to know basis. Furthermore, having insight into user activity through logging and monitoring, implementing a robust data loss prevention program, and having strong detection and response capabilities can help keep Malicious Marvin at arm’s length within your organization.
Conclusion
Protecting your organization against an Insider Threat requires that you first understand what those potential threats might be by familiarizing yourself with Insider Threat Profiles. Disgruntled Debbie, Oblivious Oliver, 3rd Party Patrick, Terminated Tina, and Malicious Marvin can cost your company millions of dollars if gone unchecked. This list provides insight into some of the most common insider threat profiles but remember that there are no limits to the motivations and profiles of Insider Threats. Anyone from business colleagues to your cyber security team could potentially pose a threat. This makes having a robust cyber security program based on the principle of “defense in depth” essential to stopping the insider threat.
Dr. Izuakor is the Senior Manager of Global Security Strategy and Awareness at United Airlines. She plays a critical part in embedding cyber security in United’s culture by training the global workforce on cyber security, supporting execution of the organizations security strategy, and developing the teams’ talent pipeline. Prior to this, she led numerous security functions from vulnerability management to handling legal implications of data security. She also independently helps corporations solve a diverse range of strategic cybersecurity challenges.
by Patrick Sullivan, Contributor
By understanding what Workspace as a Service (WaaS) has to offer your End Customer, you can ensure that you’re reaching the customers who will benefit the most from the cloud. WaaS has so much to offer to so many. But, who is the ideal prospect?
So often we are asked, “What’s the best vertical for your solutions?” and, “What industries do you typically target?” or, “What type of companies can WaaS help?”
WaaS has practical applications across every vertical and just about every size business. This widespread versatility gives our partners the flexibility to develop their solution and messaging for the verticals they are already targeting, or to focus their marketing and sales as broadly as they want.
Using the Core-4 to Find the Ideal WaaS Customer.
When evaluating a prospective WaaS customer, look for the Core-4, which will help you zero in on the ideal cloud workspace customer. If the prospect answers “yes” to any of these four questions, then you have a winner:
1. Will you require a server refresh or other large IT project within the next 12 months?
Especially this year as Microsoft will sunset Windows 7 and Windows Server 2001/2008 R2 next January, so many companies are going to have to decide: expensive fork-lift upgrade, or easy and inexpensive transition into the cloud. End Customers hate IT projects, and with the cloud, you can eliminate the majority of them, saving them money and resources, and building your cloud business in the process.
2. Do you have employees who work remotely? Or does your business have multiple locations?
In today’s global business environment, companies are turning more and more to hiring remote staff, often outside their geographic footprint. Consider a company who hires Susan whose sole responsibility is to meet with customers; any time she spends in the office is just wasted time. Or, what about a business who needs Grant’s specific expertise, but he lives in Seattle, hundreds of miles away. In both cases, the staffers need the same accessibility as anyone working from the office. In both cases, the company’s IT needs to have control over their technology. Cloud Workspace simplifies both of these, making them an easy reality.
3. Do you have extensive security needs?
Think about a small bank, finance company or insurance agent. These are small companies, but they store and share sensitive client information. Security is paramount for them. At CloudJumper, we work incredibly hard to ensure our solutions are inherently secure. Additionally, we have a number of optional security add-ons that help your End Customers who need even more.
4. Is your company’s IT function larger than your IT team can support?
This can come out in a number of ways. Of course, if they have big security needs, but maybe, they also have numerous software apps to manage and maintain. They might have tight IT requirements for maintaining certifications or franchise agreements. Maybe they have a mix of OS and devices that all need to connect. The list here is endless, and no doubt your prospects will share items they simply would love to off-load to the cloud.
Always Has Been, and Still It Remains, it’s the Core-4
These are the four prospect characteristics that so easily translate into a sale, and they always have in the 20 years we have been providing a WaaS solution. You will find them in businesses across every industry, every vertical, every part of the world. Understand them, recognize them, and the sale is yours! It’s just a natural fit.
By understanding the ideal WaaS customer, you will more easily grow your business in the cloud, and boost your sales, profits and the stickiness of your customer base. Especially as you are just starting to build your cloud business, start with the Core-4. Soon, you’ll find yourself supporting your customers in ways no on-prem server farm can handle.
Patrick Sullivan is the Channel Sales Manager for CloudJumper who uses his cloud expertise and business acumen to guide MSPs as they create and grow their companies in the cloud. His support helps them build an IT cloud solution that saves their end customers money, time and hassle. Patrick has been with CloudJumper since June 2015 and has been very successful working helping his partners build their businesses in the cloud. Prior to joining CloudJumper, he honed his business development skills working in the equipment finance industry for more than 8 years. In 2005, Patrick graduated from New Hampshire University with Bachelor of Science in Business Administration.
You don’t think it can happen to you until it does.
The 20’s clients can be up and running the day after a disaster.
One of our MSP partners, We Are Service, saved the day for Ryan O’Neal Autos, under incredibly unfortunate circumstances. After suffering a devastating fire, they had the client back in business with phones and computers hooked up; with all of their critical data restored, the following morning. They lost hours of business, not days, weeks, or months!
Here’s the full story, from the dealership:
On Thursday night, March 23, 2017, our dealership had a devastating fire that began around 9:30 pm. The prompt response of our brave firefighters was crucial, but equally important were the critical actions taken by our IT service provider, We Are Service.
While the building was still burning, I called We Are Service and James Taylor came to the scene at once. James entered the building once it was safe, and with the fire department’s permission. James ‘rescued’ our server first, and then several other computers. Moving quickly, we were fortunate to be able to secure a temporary location to set up business next door in the unused space of an auto detail business.
James and the We Are Service team worked through the night restoring our data to a temporary server, setting up telephone service, and reconfiguring some loaner computers to operate at the new location before our business even opened that Friday, March 24th. With some equipment and furniture loaned to us by Amarillo National Bank, and with We Are Service’s continuing efforts, our business never was closed. In spite of the fire and total loss that was reported widely in our local media, we experienced zero down time. It’s nothing short of a miracle that with the We Are Service team’s monumental efforts and exceptional customer service, our business was up and running the following morning and we were selling cars uninterrupted!
Of course, when we constructed our new building last year, James and his team came out and got everything wired and set back up for business. With 24/7/365 help through The 20, We Are Service is our managed IT department. Taking their advice on the new location, we continue to save money to this day with our new VoIP phone system they recommended and installed.
James and We Are Service were strongly recommended by one of our clients several years ago and holy smokes we are so fortunate that we took that advice!
Enjoy the video testimonial from Ryan O’Neal Autos’ Sales Manager, Michael Conrad, below:
I think we’ve all seen those virus alerts to some degree or another that pop-up on our desktops telling us that we’ve been infected. They’ll typically pretend to be from legitimate companies like Symantec or Microsoft (in some cases, even using a fake Microsoft logo to establish credibility), and they always want you to call a fake number — which leads to paying money for a fake service.
I’d like to believe that anyone reading this blog is someone who can detect this kind of scam, but regardless, whether you’ve fallen for this in the past or not, new information on the source of this costly annoyance appears to have come to light.
And it takes us all the way to India, thanks to The New York Times.
The article begins by telling us that 1 out of 5 people who receive such alerts tend to contact the fake tech support centers, while 6% of users in general actually pay for the fake services – which is crazy in and of itself.
Nothing about those alerts look legitimate, but hey, there are A LOT of people on this planet…
The meat of the piece points to Microsoft and how they helped police trace who was behind these large-scale operations. Apparently, these scammers have their roots in New Delhi, the capital of India, which is also the epicenter of call centers in general.
According to the software giant, more than 11,000 calls per month about fake security warnings were being received. And many people as a result, lost significant sums of money to the fraud.
On Tuesday and Wednesday, police from two New Delhi suburbs raided 16 fake call centers and arrested more than 50 in connection with the scam.
The Scam
Fixing the non-existent virus could involve calling a tech support center, where an operator would talk a victim through a fake fix and then charge them for the work. In other cases, the bogus tech support team would call their targets themselves and pretend to be a Microsoft employee, bringing to their attention a virus or false claim that his or her system could have been hacked. Eventually, they ask for anywhere from $99 to $1,000 to fix the problem that doesn’t exist in reality.
Courtney Gregoire, an assistant general counsel in Microsoft’s digital crimes unit, perhaps said it best when she was quoted as saying, “This is an organized crime.”
No doubt.
The scam is incredibly lucrative according to researchers at Stony Brook University. They published a detailed study of fake tech support services last year that estimated just a single pop-up campaign, spread over 142 web domains, could bring in nearly $10 million in just 2 months.
Microsoft said it was working with other tech industry leaders such as Apple and Google, as well as law enforcement, to fight the digital epidemic, which is migrating beyond the English-speaking world to target other users in their local languages.
Microsoft has also published advice about ways to spot the fake calls and avoid becoming a victim.
How was your Thanksgiving? Great, we hope!
How about Black Friday? Cyber Monday? Are you in to those type of things? Personally, I typically avoid these shopping rushes in general, but there’s no question they’re incredibly popular and overwhelmingly successful.
So if you do participate – heck, even if you simply plan on shopping at all online this holiday season (like 100% of us do), you have to beware: scammers want in on that holiday gift budget.
Shoppers are expected to spend roughly 4.1% more this holiday season than in 2017, which equates to around $720.89 billion, according to the National Retail Federation.
Good. Night.
Can you imagine the criminal element’s attraction to a number like that?
Last year, according to Payments Next, online fraud attempts increased by 22% between Thanksgiving and New Year’s Eve. Between Thanksgiving and Cyber Monday alone, malware infections jumped 123%, according to data released by Enigma Software Group.
Red Flags
Just as you wouldn’t want to buy a designer watch from a guy in some dark and creepy alleyway, you don’t want to buy anything online from a seller you haven’t fully investigated.
One place to start is by searching the BBB’s online directory, which can tell you if the business is accredited, and whether or not the BBB has received complaints.
Truth be told, you should probably check to see if they’re even in the database. Because if not, well, that’s a concern. You can also do a general Google search which will pull up a lot of information about that company and their website.
In addition to checking the Better Business Bureau listings, the Federal Trade Commission says to make certain the website includes a physical address and a phone number, and verify them. That way you have a place to contact should things go wrong.
Fake Shipping Notices
This year the BBB is also warning of fake email delivery notices that say you have a package on its way.
It’s probably common sense that an actual delivery company isn’t going to email you about a package, right? How would they have your email address? But I suppose you can’t be too careful during the time of year where you’re conducting online orders left and right. Amazon emails begin to run together and suddenly an email claiming to be from a delivery service doesn’t seem all that strange…
But you have to keep your head on a swivel. DO NOT click on any links. It’s most likely malware, or at the very least, going to ask you for personal information like credit card numbers or addresses. Before you know it, you’ve just participated in the theft of your own identity.
Legitimate carriers will never ask you for personal information through email.
Santa’s Phishing
Several trusted companies offer charming and personalized letters from Santa, but scammers mimic them to get personal information from unsuspecting parents. Check with the BBB to find out which ones are legitimate.
The big risk here isn’t that your kid won’t hear from Santa, but that you’re providing key details to a phisher who will use it to perpetuate other fraud or identity theft.
Charity Scams
Did you also know that scams come with philanthropy?
The holidays are a wonderful time to support your favorite causes, but to ensure that your funds go where you desire, you’ve got to make sure the group is legit.
According to nonprofit rating site Charity Navigator, roughly 40% of all charitable donations are made in the last few weeks of the year. So, you better believe scams pop up in the form of donation solicitations via email, social media and text.
Common charity scams include look-alike sites or imposter websites, phony emails that are “phishing” for personal information or giving a check or cash to an individual as opposed to an organization.
The BBB’s Give.org is a great resource to research legitimacy.






