How to Implement Zero Trust for RDP & RDS
TruGrid has brought us an informative guide on how to add a layer of security to your client’s RDP experience. This approach is great for a client that values security over everything else, or clients who have been hit previously by ransomware, especially via RDP exploit. See if a zero trust RDP environment can benefit you and your clients’ peace of mind.
Microsoft Remote Desktop Protocol (RDP) is one of the most common ways to achieve effective Work From Home & Remote Work. Zero Trust for RDP can help prevent ransomware and data leak between remote users and office networks.
This article presents two ways to implement Zero Trust for RDP access and connections. One method is via Active Directory GPO. Another one is via Endpoint Policy enforcement. In order to follow the recommendations below, it is assumed that RDP itself is not directly exposed to the internet. If you are exposing RDP to the internet, there is a link at the end of this blog with recommendations on how to secure RDP from internet attacks.
What is Zero Trust?
Zero Trust is a security framework popularized by Google that shifts access controls from the perimeter to individual devices and users. It allows organization to not necessarily trust any remote employee or device, while granting just the required access to authorized resources on the company network. The end result allows employees to work securely from any location without the need for a traditional VPN – which allows too much trust and is difficult to secure. Zero Trust can be applied to many facets of network security, including RDP access.
For example, when RDP access is granted into internal Windows desktops via Microsoft RD gateway or other secure means, the default RDP settings at the remote user endpoint allows several devices on the end user desktop to map into the internal network. This can lead to data leak or theft, or successful ransomware attack.
Using Active Directory Group Policy to implement Zero Trust for RDP
If nothing is configured in Active Directory, the remote end user MSTSC (RDP) settings will determine what happens with RDP access device mappings. By default, MSTSC (RDP) allows drive mappings and printer redirection. To control these, please use Active Directory GPO as shown below.
1. On internal network Active Directory domain controller, open Group Policy Management Console (GPMC). Create and link a new GPO at the OU level containing internal computers that you wish to safeguard; or at the domain level and restrict it to a security group containing internal computers that you wish to safeguard.
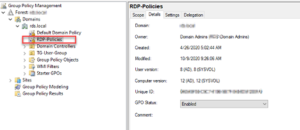
2. Edit the new GPO and navigate to the following path. Apply desired settings as shown below.
Path: COMPUTER CONFIGURATION\POLICIES\ADMINISTRATIVE TEMPLATES\WINDOWS COMPONENTS\REMOTE DESKTOP SERVICES
Restrict clipboard, legacy ports, USB ports, plug and play devices, smart cards, and disks
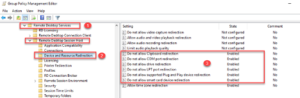
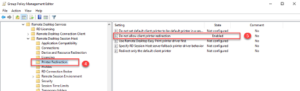
With above GPO settings, computers that these settings apply to will be safeguarded from data leak, data theft, and ransomware attack originating from the remote user network and endpoints.
Using Endpoint Policy to implement Zero Trust
While the above GPO option can be effective, unless enforced on all computers at the domain level, IT Admins may need to constantly manage which internal computers these policies apply to. Another way might be to apply the policy at the remote user network / endpoint. With this approach, any computer that the remote user is granted internal access to will be secured against data leak, data theft, and ransomware attack emanating from that remote user endpoint and network.
Endpoint Policy is also very effective for multi-cloud and hybrid deployments regardless of location of the RDP hosts. It is an effective way to ensure that policies are uniformly applied to remote workers / endpoints regardless of which company asset they connect to.
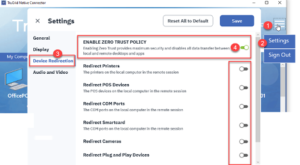
To implement Zero Trust for RDP at the remote user / endpoint level, organizations can use TruGrid SecureRDP software. With TruGrid SecureRDP, ADMINS can click a single button that blocks all device redirection between remote user / endpoint and company network.
Using TruGrid SecureRDP software to implement Zero Trust