How B2B Sales Have Changed for MSPs
Technology has continued to increase at a dizzying pace. A decade of knowledge and expertise can be rendered obsolete in less than a year if you don’t keep up. A standard business can coast on what used to work, but they hit a hard wall sooner than later. The nature of IT has changed, so it’s only natural B2B sales strategies should change too.
Business to business (B2B) sales have changed for MSPs. Technology has gotten too complex for non-dedicated resources, many sales packages focus on what they offer versus what problem they solve, and there’s a tendency for businesses to move towards risk reduction rather than optimal efficiency. These aren’t the only factors, but they are major ones.
Each of these factors impacts B2B sales in a different way, though they all contribute to the overall picture. Some of these will be relevant to your clients, and others won’t. There is not a silver bullet for B2B sales, but there are tricks and techniques which can increase your odds.
Understanding and the Complexity of Technology
When you run an MSP, you have to balance keeping up with technology and keeping your business running. One feeds into the other, but to most businesses, technology is just a tool and not a trade. You see the dividends from staying up to date, but your clients usually just see unnecessary expenses.
It costs both time and money to keep up with technology. While individuals (hopefully) understand technology at the business, the business as a whole has no idea what goes into their day-to-day functioning. Your job when trying to sell is to become the “individual” or “team” a company can rely on for their technology needs.
Selling a client on filling their technical needs is a lot more future proof than selling on support only. What happens when the client makes a terrible decision and you’re contractually obliged to support it? If you can actually walk the walk, you want to be pushing clients towards things which help make their jobs easier, and your support more efficient. You want to paint your service as a shortcut to modern technology rather than just a new generation of break-fix.
Selling Solutions
Any given task at a business requires a complicated number of systems which should be as transparent as possible for the end users. Some businesses may expect their internal IT to work in conjunction with your offering, but those are less common. Most businesses just want someone to take IT off of their plate.
The users don’t care how the system itself works, just that it does. Most want to use it to do their jobs without having to think about it. Sell them on what a solution does rather than on what makes it work.
Simplify your offering into things that make sense for your clients. Most clients don’t care that the cloud environment you’re selling them on has SSDs rather than spinning rust; they just care it’s faster. The more technical terms can help them feel in the know, but let them know what a solution means for them specifically to sell it.
How does your solution solve their technology needs and how does it make their jobs easier? The more efficiently you can convey this and help put it into terms explaining how it impacts them, the easier it is to sell. They’re not picking you to explain the nuts and bolts (usually), they want you to provide solutions which fit their problems.
Risk Reduction
This all fits into the trend for more and more businesses to try and reduce risk. Smaller businesses have been trying to find ways to cut costs and/or reduce risk since well before the pandemic, but 2020 has made it that much more important. How can you reduce the technical risk your client has in terms of time and money?
The cloud didn’t work out as economically cheaper in the beginning, but it reduced the technical hurdles and cost to implement and maintain a solution for people who didn’t have the infrastructure in place. The risk reduction came in the form of preventing technical risk during implementation, reduced the dependency on local resources, and the fact it could prevent unexpected costs (you don’t need to replace hardware) was worth the additional cost per month. You can run a home brew “cloud” for cheaper than many solutions (though it’s getting harder with the razor thin margins), but even professionals tend to favor the cloud.
By abstracting a solution into an offering, you reduce the cost to maintain it. If a drive pops on a cloud environment, it’s the host’s problem. Companies want the liability and risk pushed off onto someone else. How can you be that solution without fronting too much of the risk? Becoming the glue which connects their disparate systems into one platform can be the offering they need.
Application and Practice
How do your offerings look and what solution do they provide? What itch do they scratch and how do they benefit a potential client? If you can’t answer these questions (even at a surface level) instantly after learning about a business, you need to reconsider how you’re doing things.
Another consideration is who you’re dealing with when selling to a business. A business can be composed of one or more different individuals with different levels of experience and knowledge. How do you explain your solution to who you’re working with without compromising what it does?
On the other hand, if someone you’re dealing with just doesn’t get it, what’s stopping you from getting in touch with someone else? Getting your foot in the door in the first place tends to be the hard part. Done right, you can seal the deal by targeting a different individual in the whole of the business.
Even businesses with dedicated IT staff may want to outsource parts of their business. If you can’t win the whole business, what’s to say you can’t win a part? Companies with full help desks may still hire an MSP to handle the pieces they don’t want to manage. The question then becomes is it profitable enough to do?
This list isn’t exhaustive, but it touches on the biggest weaknesses of many MSPs’ current B2B sales strategies. Clients may want you to fill the gap the last technical company left, but you won’t get far if you don’t think in terms of how you can solve their technical problems, especially the ones they’re unaware of. Technology is complex, and they want to shop on what makes their job easier, not what it does in absolute terms while reducing their risk to unpredictable expenses.
Once you find how to put these pieces together, you sell on the value you and your service provide rather than selling a gear in the system. Make yourself indispensable to your client while making your sales easier. A gear can be easily replaced, but the whole system can’t. Become the force which helps your client realize and manifest their technical dreams as a reality and both of you will profit.
Ready to 10x your MRR? Contact us today to see if your MSP is a candidate for The 20 membership!
Meet Alexis Williams, Marketing Coordinator
What do you do here at The 20?
I am a Marketing Coordinator and I work on PR and coordinating all content.
Describe The 20 in three words…
Family, Fun, Exciting
As a kid, what did you want to be when you grew up?
Growing up, I always wanted to be a fashion designer. I had a sewing machine and a notebook with all my designs.
What’s the most challenging thing about your job?
The most challenging part would be the fact that I want everything to be perfect.
What do you consider your greatest achievement?
I would consider my greatest achievement graduating with two Bachelor’s degrees in four years. #GoMeanGreen
What do you think is the most important quality necessary for success?
I think the most important quality for success is believing in yourself. If you don’t believe in yourself and put your best foot forward, why would you expect others to?
What do you like most about The 20?
The people, I have met the best people here and gained great friendships! They truly make everyday at work fun!
What do you like to do in your spare time? / What are your hobbies?
In my spare time, I am a proud Netflix binger and I love baking! I also happen to be a sneaker addict. With that being said, I spend a lot of time online shopping haha
Where are you going on your next vacation?
I’m hoping to go to Jamaica sometime next year but we will see!
What’s your top life hack?
Oreos. I swear they are the cure all for a bad day ????
Interested in working with Alexis at The 20? We’re hiring! Check out our Careers page for more info.
A Guide to Long Tail SEO for MSPs
Long tail SEO is one of the simplest concepts in SEO, but can also be one of the most confusing in practice. A long tail search is one where you have a non-trivial search to get more specific results. For instance, if you want to search for a backup solution like Unitrends, you might search for “Hyper-V cloud backup solution”. You (or your prospective client) can always use some other non-trivial set of descriptors which spells out a similar combination of factors the solution offers (for instance “VMWare” or “SaaS” in the mix), and this is what makes long tail SEO so valuable and so difficult.
Long tail SEO relies on you optimizing your content for long tail searches which would actually bring in the right audience. This form of SEO combines many techniques which help with all forms of SEO. You’re doing keyword optimization many times over while incorporating live data and reacting to changes. Let’s break long tail SEO down further, see how to target for long tail searches, then we’ll dive into when and where to do it, and how to make it work for you.
Long Tail SEO
If you’re a business, someone is searching for something that describes your business or what it does the longer the tail gets. Done right, this means that you get more prospects naturally. On the flip side, if it’s done wrong, you just get raw traffic with no real value looking for something else entirely. It works because the search engine becomes an artificial filter for your incoming demographic.
Some searches are worth more than others. Singular search terms (or short search phrases) are saturated or generic and there really isn’t a way to get ahead because the search itself is generic. The goal of long tail SEO is to focus on winning more niche topics that are less contested. Each term added to a search adds a filter which reduces the number of viable results. The more they zoom in, the bigger you get, but only if you’re in the continuously shrinking window.
We’ve touched on the basics of long tail SEO, but there’s a lot that goes into the process. Long tail SEO needs to be calculated based on how your clients search. Who are you targeting and what are they searching for? What keywords do you see from Google Search Console or similar and how can you put them together? Keywords are important, and knowing what keywords your prospects actually use for plain searches is the first step in making long tail SEO work.
You also need a way to track the results. If you haven’t used Google Search Console (or similar), you need to start now. An analytics system (Google Analytics, Bing Analytics, or even something like Koko Analytics) will provide insight into the metrics which will help you measure what people are searching for and where they’re going.
Measuring CTR and Other Metrics
These tools enable you to begin tracking the CTR (Click Through Rate) for a given search as well as the landing page. If 3 of your pages mention backups and associated terms, is one faring better than the others? If so, why? To optimize SEO, you need to understand what is actually working, then figure out why it’s working. Or, if nothing works, you need to figure out how to make the right changes.
Google Search Console gives you the query, clicks, impressions, and the search position for any term which involved your site. For our purposes, we can treat the ratio of clicks to impressions as the CTR for the site. Some organic searches will have a great ratio (some can be as high as the double digits for a percentage), others not so much (<0.01%). Position is important as well, with the higher the better, but improving your ratio will improve your position most of the time too.
Google can also give you a similar break down for any given page, and the clicks, impressions, and position it has which can get you a similar search CTR per page. Putting these two calculated metrics together won’t give you exactly what ratio you’re getting searches for specific pages, but you can combine analytic solutions to approximate this.
No set of numbers when working with search and analytic data will ever be absolutely right. If I compare the numbers from Google Analytics with the numbers from Google Search Console, the numbers between them aren’t usually going to add up exactly. The data is collected, culled, and combined in different ways so you get different results. Work off the trends and ratios rather than getting maddened by the fudge factor.
Targeted Keywords
These calculations give you how people search for you (keywords), where you show up (searches), and how individual pages show up. To improve your SEO, you ideally want to reconcile the first and the second sets of terms to be closer. The closer, the better your search does and the higher your natural position goes (usually).
What keywords define your MSP and your business? What keywords define what your current and ideal clients expect from your MSP? This is the specific part which gets a bit fuzzier for MSPs. You also need to consider what value each page adds and what people would search on it.
When targeting keywords, most businesses are playing with a level field. MSPs usually have a mix of B2C (Business to Consumer) and B2B (Business to Business) considerations which can be further exaggerated by the fact that peers and vendors exist across a spectrum of technical knowledge. Content has to be accessible and usable to both sets as a whole though. This isn’t to say you can’t target more jargon-laden terms, but you need to explain them.
Most clients won’t know what RAID is (or think it comes in a can), but a vendor is going to be confused if you never reference it directly in more technical pages. A page obviously for consumers won’t matter, but both sets of content need to exist and be targeted. Create your own information and writeup on topics which come up continuously with technical and lay versions.
How to Improve Long Tail SEO
Target the keywords which work for your business first. Build them into phrases which clients, vendors, or whoever you want to bring in would search for. Once you have an idea for the keywords which work well (this involves either looking at your metrics or keyword research), you can begin embedding them in content.
Apply these techniques like you would keywords to any content as we mentioned in The Top 13 Easiest Ways to Improve SEO for MSPs. You want content to include these words abundantly, but naturally. For instance, in this article, we have used the term “Long Tail SEO” over and over, but in a way where it flows.
SEO all works off of content, but there are little tricks which can help give you an edge. Use them to your advantage and target the keywords you need. For certain phrases, feel free to include them as is or with grammatical or filler words in between. If “MSP high uptime backups” is how people are finding you, feel free to work that in. “Our MSP prioritizes high uptime and safe backups,” or similar on an About Me page can help solidify that search.
What Not to Do
You can’t work every term, keyword, or phrase in everywhere. There are people who try, but it ends with the content either taking enough of a hit searches drop off, or else it becomes buzzword bingo. You can cheat the algorithm but not the reader usually. Target the keywords and phrases which actually matter and actually occur per metrics and research.
Prioritize the things which are the easiest to implement and provide the most value. Just because a keyword can get you to the number one position of an extremely cryptic search doesn’t mean it’s good. You need the right mix of a niche with accessibility.
Don’t omit cross-referencing terms and researching similar terms when prioritizing your keyword targeting either. Basically, how can you save time and effort by batching search terms? If “email parser” is a common term with many okay searches, it can be viewed as worth the same as one term which has a single usage and much more success. Keep in mind that there is a bigger picture when creating a strategy.
Don’t try to capitalize on searches which will conflict with your brand. There’s no such thing as bad press is a marketing cliché, but whether it’s true or not is different question than how SEO works. If you sacrifice parts of your content for the sake of targeting something else, you’re typically robbing Peter to pay Paul for your SEO. It can work, but it’s way beyond the scope of this article.
Making Simple Content Adjustments
I won’t touch on all the standard SEO techniques in here. SEO is SEO, the only difference is the focus and the purpose of each strategy. Good content gets you good SEO, but like anything, there are things you can do to get the most bang for your buck and “good” is often subjective.
If you see a phrase in the search console which is bringing in traffic, try to work it in, or work in the keywords. If a synonym beats out what you’re using, work it in. If your clients find you under “support desk vmware comptia certified”, but you use “help desk”, consider at least adding in “support desk” on any page the help desk is mentioned. I would also increase references to the rest of the terms (if relevant).
If a singular term is showing up with many variations, for instance: “vmware installation msp”, “vmware certified msp”, “vmware virtualization msp”, etc., and is bringing in a good amount of traffic, use it where possible. You can continue to expand on this as the tail for the search query gets longer and longer and work these things in as you go forward as long as the content stays relevant to the searches.
Deeper Content Strategy
As you move forward with your strategy, you’ll reach a point where there aren’t small things to change anymore. You need substantial rewrites, content is deprecated, etc. If things still kind of work, it can be worth a little cleanup first to improve results while you get the time to go deeper.
Long tail content tends to be more long lived for relevance, but less relevant overall. That being said, some things do have a lifespan. There aren’t many searches for CAT3 anymore, but there are plenty of references to its installation or usage left. While this example is neutral, old content can eventually hurt you if left unchanged and unchecked.
What content do you have which is completely obsolete? What just needs a change to something more modern to be relevant? This gets more complex with tech articles. A guide to fix a DOS-era POS system may still be relevant to why some clients hire you. Context makes the difference between your guide being a relic and it being proof of skill. Update your content with context as to why it’s still relevant. Search engines tend to favor content which is updated, so by adding context, you show the content is being maintained, and make it stay useful for readers.
Content that no longer serves a purpose needs to be culled. There’s probably going to be some useful pieces caught in the crossfire which need to be heavily reworked or redone. The weaker your search rankings, the more likely you have a lot of work to do. Sometimes, this may even coincide with an entire redesign of the site. You have to run the numbers and weigh the cost of redoing content to the reward it can bring.
Going Forward With Long Tail SEO
Understanding what long tail SEO can do for your business is the first step in using it. Research and analyze what people search for, what they search to find you, and the intersection between these. Calculate what each keyword means to your site and searches for you.
As you learn and apply these principles, you’ll possibly reach a point where minor changes just don’t work anymore. Sometimes you need to make some massive changes or effectively start over to get the results you need. Start with what gets you quick results and move on as possible.
Gradual steps will be more efficient for most working professionals than a huge changeover all at once. This gives you a chance to see results without a large investment. SEO is only as good as the content and strategy behind it, so figuring out what actually works first can make the next steps easier. Researching and testing works better in an iterative process.
Long tail SEO isn’t the only thing to focus on, but it can easily be combined with other techniques. You won’t hurt your SEO shoring it up to make longer queries lead to your content. The process of shoring up long tail SEO is going to incidentally affect “standard” SEO. As you work through long tail SEO, you get the data and metrics to fix everything else.
SEO is SEO as I mentioned before, the difference is in the strategy and implementation. Focusing on long tail SEO doesn’t come at the expense of other strategies, it enriches them. Done right, you aren’t trading one strategy for another, you’re batching the work and doing a little extra analysis. Even if you can’t apply everything, just starting the process can be enough to make huge strides with SEO.
Meet Trent Milliron of Kloud9 IT!
Tell us a little about your MSP…
Kloud9’s headquarters are in Cleveland,Ohio and we have offices in Cleveland, Akron, and Columbus Ohio. We started in 2006 as a break-fix company and began all inclusive services in 2010, as a way to assist businesses in budgeting but also as a way to have better control over tier infrastructure to prevent problems from occurring instead of getting calls because something is broken.
How long have you been a member of The 20?
Around 6 years
Why did your MSP originally look to partner with The 20?
Buying power with vendors, also done for you integration with the vendor tools as well. Meaning you are buying into a set of tools where everything is working together as it should. Going further on this, also buying into sales and operations processes as well that work. And a community.
Tell us about the biggest change in your business since joining The 20.
We have been able to streamline our service offerings and present them in way that increases revenue.
What do you like most about being a member of The 20?
The camaraderie with likeminded individuals who want success.
What do you think is the most important quality necessary for success?
Always work on increasing revenue. If you are not growing, you are shrinking.
What are your biggest business challenges?
Developing Processes and Employees.
What are your areas of focus for 2020?
Expanding our service offerings in order to increase opportunities for our sales team. Also adding a defined cyber security service
What advice would you share with an MSP looking to scale their business?
Delegate, Use Metrics, and Spend Money on Marketing.
What book are you currently reading?
Scaling Up. Get A Grip.
Favorite blogs / podcasts
Joe Rogan, Jordan Peterson, Dennis Prager, Candice Owens, Dave Rubin
Interested in becoming a member like Kloud9 IT? Click here for more information!
Search Engine Optimization (SEO) can be a daunting task for anyone who doesn’t have a background in marketing. SEO is how you get your site or business found. While following the basics will almost always be the right choice, there are tricks which can help an MSP get an edge over the competition. Let’s look at the 13 easiest things you can do for your MSP (though a lot of this advice applies to most businesses) to improve organic SEO.
Keywords
When someone performs a search, they use keywords or important terms to try and find a specific result. This is the foundational concept behind how a search engine works. Keywords used to live in special tags or be derived from the title, but computing has grown and search algorithms have gotten exponentially more complex. Almost everyone is familiar with keywords, but how they work has changed substantially. Keywords don’t just live in a title or a tag, they live in the content.
1. Targeted Keywords
What does your page or solution provide and how would a prospective client find it? This is the most important question to answer before even starting to create content. Once you have an answer, you can begin planning keywords which are relevant. For instance, if you’re writing about backups, you want to target the core keywords for backups, but also the specific keywords which help qualify your article.
We use terms like backup, BDR, and disaster recovery to cast a wide net for generic information on backups. This isn’t enough though, we want to get some of the long-tail searches even if they’re tangential. We work in terms like cloud, on-premise, virtualization, tape, etc. to make this content more appealing to more search users (and ideally anyone reading as well). Target keywords, but make sure they’re relevant to your content. This is the foundation to everything you do with SEO for any content.
2. Use Synonyms
You may have noticed that a lot of those keywords I mentioned seem a bit redundant. Backups and BDRs are arguably the difference between rectangles and squares. A search engine algorithm might use synonyms to help a user direct their search, but an exact match is still worth more. Pepper in synonyms and similar terms where they fit to cast a wider net.
This is especially important for MSP’s since your client may not always know what to search. They don’t necessarily know what DRaaS is before they talk to you, but they do know what they want (or at least have an idea) when they search (and it may be as vague as “to have backups”). The more generic or simple terms you can work in (especially early on) the more likely you are to get and retain a prospective client. Spicing up terms benefits more technical content as well.
Links
Inbound and outbound links can influence search rankings. Who you link to, and who links to you will impact your search engine ranking. Links are still important, but link farming (arbitrarily putting links on sites, or link farm sites to manipulate search rankings) is a quick way to get dropped. How can you squeeze an extra ounce of link juice (the value of a piece of content based on inbound links) out of your content without crossing a line?
3. Internal Links
The quickest and easiest way to increase link juice (which improves your SEO) is to link to your own content. You can’t just spam the same links or random links; they have to fit the content. Internally referencing your own blog or assets (in a way which contextually fits) is an extremely easy way to get an edge without any real downside.
Got an article explaining what something is? Link to it on other pages where you use the concept. Don’t be afraid to edit older content to add links to newer articles. This gives clients (or peers) a way to dig deeper and stay on your site while (ideally) deriving value.
Content
Modern search engine algorithms don’t just look at keywords and titles, they look at the entirety of the content and everything on the page. The main “trick” to good organic SEO is to just make better content. What question does your content answer and for whom? While good content is the main key to good SEO, that doesn’t mean there aren’t things you can do to improve the odds or make content shine even more.
4. Clearing Assets
Any asset which you use needs to be legally obtained or applied (the license matters). You can’t just download an image off the internet and use it. This seems like it would be common sense, but there are countless people who don’t follow this rule. If you used to do it before you knew better, fix it now.
It’s arguably content theft, but to top it off, it will hurt your SEO. It can also get you dropped entirely or even a DMCA takedown notice. Clear all assets you plan to use and make sure you have them licensed or use something with a free or public domain license. Attribution is also important depending on the license.
5. Subheadings and Organization
Headings, subheadings, and their organization can also impact SEO. The “ideal” at present is between 100 to 300 words per subheading for most content. These little changes in organization can enrich the keywords a search engine picks up on and in turn increases your SEO.
Most search engine algorithms give preference to content which is emphasized in some way. The most common way to do this is via test markup like em or strong tags, or h header/title tags. Make sure you highlight things which are important. You don’t even need to rewrite the whole thing. A little extra organization of content and subheadings leads to a boost in SEO.
6. Content Consistency
A bad verse in an otherwise great song can ruin the whole thing. Likewise, inconsistent quality can be as bad as consistently bad quality. Having poorly written content and keeping it for a misguided attempt at optimizing keywords or similar hurts your SEO. This can be a paragraph or a page.
This isn’t a judgment on your writing, but what content do you have which is (or has since become) wrong? An article about Windows Server 2003 won’t hurt anything, but an article about best practices for wireless security from the days of WEP will. It isn’t just dated, it can be harmful.
If everyone who Googles “best MSP near me” clicks your page and jumps to the next result because the content sucks, Google’s algorithm takes notice. If some of your content is bad, it can tarnish the rest too though. Where a reader lands can be as important as whether they even click. If content doesn’t work anymore, pull it. Make sure that the content you have stays consistent with the message you’re trying to broadcast to your clients without confusion.
Content Length
A long article has a different impact on SEO than a short article. A short article weekly has a different effect on SEO than a long article sporadically. You can create countless comparisons but the rule of thumb is that more is usually better. More content more often, or more words on a single article.
7. The Magic Word Count
Most search engines hit a soft SEO plateau around 1,000 to 1,500 words. The bigger ones tend to favor a bit more, usually 1,200 or more is ideal. Google, Bing, and basically any other modern search engine is going to reward you for longer content, you just hit diminishing returns from it.
The one thing to take of note of though is that substantially less than 1,000 word articles (say around 800 or less) tend to be worth less for SEO. Some content doesn’t need to be that long and trying to force it just harms it (like a contact page). SEO rules, especially this one, tend to be a bit like English spelling rules. The rule applies until it doesn’t.
Conclusion
SEO is SEO in any industry, the difference is how valuable a specific factor is over another. These tools and techniques work as basic tools for all kinds of specific SEO. A local business will benefit less from a global presence. One of the big differences for SEO for an MSP is the focus on both local and general reach.
You want your company to be the first result locally for prospective clients, but you also want vendors and other businesses to be able to find your site. These give you opportunities for growth and development of your business.
How to Implement Zero Trust for RDP & RDS
TruGrid has brought us an informative guide on how to add a layer of security to your client’s RDP experience. This approach is great for a client that values security over everything else, or clients who have been hit previously by ransomware, especially via RDP exploit. See if a zero trust RDP environment can benefit you and your clients’ peace of mind.
Microsoft Remote Desktop Protocol (RDP) is one of the most common ways to achieve effective Work From Home & Remote Work. Zero Trust for RDP can help prevent ransomware and data leak between remote users and office networks.
This article presents two ways to implement Zero Trust for RDP access and connections. One method is via Active Directory GPO. Another one is via Endpoint Policy enforcement. In order to follow the recommendations below, it is assumed that RDP itself is not directly exposed to the internet. If you are exposing RDP to the internet, there is a link at the end of this blog with recommendations on how to secure RDP from internet attacks.
What is Zero Trust?
Zero Trust is a security framework popularized by Google that shifts access controls from the perimeter to individual devices and users. It allows organization to not necessarily trust any remote employee or device, while granting just the required access to authorized resources on the company network. The end result allows employees to work securely from any location without the need for a traditional VPN – which allows too much trust and is difficult to secure. Zero Trust can be applied to many facets of network security, including RDP access.
For example, when RDP access is granted into internal Windows desktops via Microsoft RD gateway or other secure means, the default RDP settings at the remote user endpoint allows several devices on the end user desktop to map into the internal network. This can lead to data leak or theft, or successful ransomware attack.
Using Active Directory Group Policy to implement Zero Trust for RDP
If nothing is configured in Active Directory, the remote end user MSTSC (RDP) settings will determine what happens with RDP access device mappings. By default, MSTSC (RDP) allows drive mappings and printer redirection. To control these, please use Active Directory GPO as shown below.
1. On internal network Active Directory domain controller, open Group Policy Management Console (GPMC). Create and link a new GPO at the OU level containing internal computers that you wish to safeguard; or at the domain level and restrict it to a security group containing internal computers that you wish to safeguard.
Create new GPO
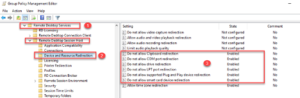
2. Edit the new GPO and navigate to the following path. Apply desired settings as shown below.
Path: COMPUTER CONFIGURATION\POLICIES\ADMINISTRATIVE TEMPLATES\WINDOWS COMPONENTS\REMOTE DESKTOP SERVICES
Restrict clipboard, legacy ports, USB ports, plug and play devices, smart cards, and disks
With above GPO settings, computers that these settings apply to will be safeguarded from data leak, data theft, and ransomware attack originating from the remote user network and endpoints.
Using Endpoint Policy to implement Zero Trust
While the above GPO option can be effective, unless enforced on all computers at the domain level, IT Admins may need to constantly manage which internal computers these policies apply to. Another way might be to apply the policy at the remote user network / endpoint. With this approach, any computer that the remote user is granted internal access to will be secured against data leak, data theft, and ransomware attack emanating from that remote user endpoint and network.
Endpoint Policy is also very effective for multi-cloud and hybrid deployments regardless of location of the RDP hosts. It is an effective way to ensure that policies are uniformly applied to remote workers / endpoints regardless of which company asset they connect to.
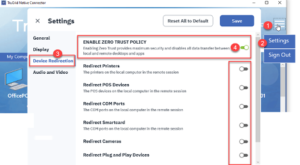
To implement Zero Trust for RDP at the remote user / endpoint level, organizations can use TruGrid SecureRDP software. With TruGrid SecureRDP, ADMINS can click a single button that blocks all device redirection between remote user / endpoint and company network.
Using TruGrid SecureRDP software to implement Zero Trust
Click here to learn more about TruGrid SecureRDP
Click here to learn how to protect RDP from internet exposure attack
Meet Kenneth Perrot, Account Manager
What do you do here at The 20?
I am an Account Manager, so I work with our current customers to ensure their satisfaction and success within the group.
Describe The 20 in three words…
Exciting, Fun, Challenging
As a kid, what did you want to be when you grew up?
I used to watch a lot of Forensic Files as a kid and wanted to be a Forensic Scientist, until I realized I wasn’t all that great at science.
What’s the most challenging thing about your job?
The most challenging part would be when there is an issue that comes up where I might not have the most expertise. Thankfully I am surrounded by great team members that I can gain knowledge from to help find solutions to those issues!
What do you consider your greatest achievement?
I would consider my greatest achievement graduating college and moving halfway across the country to a state where I didn’t really know anyone! The personal and professional growth that has come from this experience has been huge.
What do you think is the most important quality necessary for success?
Work ethic and drive. “Hard work beats talent when talent doesn’t work hard.”
What do you like most about The 20?
I love the overall atmosphere and the day to day interactions I get to have with my coworkers! The 20 employs great people who make me look forward to going to work. We also have great customers who make work enjoyable as well!
What do you like to do in your spare time? / What are your hobbies?
In my spare time I am very active! I’m in the gym 5-6 days a week, enjoy playing golf, basketball, disc golf, and tennis.
Where are you going on your next vacation?
My next vacation will be a trip back to Tampa for Thanksgiving to see friends and family!
What’s your top life hack?
Always try to be polite and well-mannered when you can! You attract a lot more bees with honey than vinegar.
Interested in working with Kenneth at The 20? We’re hiring! Check out our Careers page for more info.
Thank you for making Virtual VISION 2020 a success!
The 2020 Virtual VISION Conference featured an impressive speaker lineup, best-in-class thought leadership, actionable content sessions, channel trends, interactive peer panels, and virtual peer networking – all focused on growing your IT services business. Keynote speaker Gary Vaynerchuk, prolific entrepreneur and 5-time New York Times bestselling author, shared business growth strategy and marketing tactics. The speaker roster also included Walter Bond and Mark Manson. Hailed as the most important MSP event of the year, VISION brought together top MSPs and IT service providers for two impactful days of speakers, sessions, and networking focused on business best practices, thought leadership, and growth.
Virtual VISION 2020 Featured Sessions:
- The New MSP Landscape | Tim Conkle
- The Only Thing Stopping You is You | Walter Bond
- How to Build a Sales Pipeline That Closes Deals Consistently | Mark Elliott
- Keynote Speaker: Gary Vaynerchuk aka “GaryVee”
- Top 3 Strategies for Engaging Remote Customers | Eric Townsend, Dell
- The Law of F*ck Yes or No | Mark Manson
- Security in the MSP Space: Threats, Opportunities & Strategies to Position Yourself for Success | Matt Solomon, ID Agent
- Tightening Up Your Security Stack To Avoid MSP FUBAR | John Hammond, Huntress
- Panel Discussions: MSP Marketing 101, Making the Jump to AI, Shadow Channels
“The 20’s model is poised to dramatically disrupt the MSP market, and a critical piece of this strategy is expanding and enabling the right type of partner base in order to accelerate nationwide growth. With Virtual VISION coming to a close, we are excited for the continuous growth and to see you all in 2021.” – Tim Conkle, Chief Executive Officer of The 20 MSP.

Thank you to all of our sponsors! We had an amazing time in the virtual world with all of you and can’t wait to see you all in 2021. Stayed tuned for VISION 2021 dates at the20.com.
5 Things MSPs Need to Know About Backups
Backup and Disaster Recovery (BDR) is an entirely different skill set which builds on standard IT knowledge. You have to have a certain level of basic IT understanding to implement a BDR solution for a client, but you also have to know about how the BDR process works to make it efficient. A little bit of understanding can go a long way for putting all of the parts together.
This article covers some of the basics that any MSP needs to know about Backup and Disaster Recovery in order to understand the process. There’s more to it than just grabbing a solution and slapping it onsite. There are a plethora of options, and very few of them compete in the exact same space. There are also technical considerations which are required to make the solution work as intended.
How Should You Migrate Backups?
Migrating data is one of the most painful parts of the backup and restoration process. Data migration happens when you’re either moving solutions, restoring from backup, or backing up a backup. The source is as important as the process.
Backing up a backup tends to be the least time constrained of the three. A cold backup or similar is typically for security rather than necessity. This is where you backup the backup to the cloud or similar for redundancy. If you don’t use a cloud solution, this can be done via a simple external drive (not ideal), or a separate NAS appliance on the network. It’s best to try and convert the backup to the ideal form for separate storage at this stage. If the secondary solution doesn’t work with SQL servers, run a manual database backup and back that up. The easier it is to work with the backup of a backup, the better. You’ll need it when you least expect it.
Restoring from backup is going to be constrained by time. You want to focus on speed at this point since every second the client is down hurts their business, and potentially your relationship with them. If they use a cloud solution and have a slow connection, can you take a drive and physically restore it off-site with a faster connection? This is the step to pull out the stops for.
Moving solutions is the more nuanced migration path. You need to get the backups out of one format, and into another which is usually time intensive. Time constraints hinge on the reason for the migration. If the previous solution failed, then it might be a bit more urgent than something with a nice handover. What do you do when one of these situations happen?
What Makes Legacy Data Hard to Work With?
We know there are still people using floppies out in the wild. Older technologies don’t die until the last media or device does. Even tape is still alive and kicking (more often than it should).
You’re going to run into clients who don’t know about media degradation, or just won’t spend the money to change how things are done. The drives have been there for 10 years, they should be fine, right? Moving a client like that requires more momentum than usual.
Tape, while dated, is also extremely efficient when done right, but it’s also extremely expensive. You need to fight the momentum to “get their money’s worth” and a format which has lasted decades as an IT mainstay. The problem is when they refuse to upgrade a decades old machine and parts are scarce.
There are still places which use burned CDs and DVDs to store software versions, and places with old floppies in their drawers. What does their business still potentially rely on in a rare scenario? The data on old floppies may win a lawsuit, but only if they’re readable. I’ve been in a spot where the data on an old floppy made the difference between a deal being a good idea or a bad one, but I had to have the tools and the know-how to get the data off.
A USB floppy reader isn’t much, but a tape machine is. Some formats require special knowledge to troubleshoot. You have a cost for hardware, but one for knowledge too. The skills don’t really transfer either.
On top of all of this, backing up data is good, but you have to be able to use the data later. What do you do if nothing can read the data? Are these elements factored into your BDR plan?
What’s the Difference: Cloud, On-Premise, or Hybrid?
Each solution has its own mix of advantages and weaknesses. Comparing a cloud and an on-premise solution can feel like comparing apples and oranges, so the hybrid approach just buys both. This is fine if you have the money, but breaks down if you don’t. It also breaks down if there aren’t compatible solutions.
Cloud solutions are best in locations with low requisite data to function, and/or high bandwidth. The lower the bandwidth and the higher the amount of necessary data, the less realistic the cloud gets. Though, it’s still ideal as an alternative or off-site backup even on slower connections. These solutions tend to be most costly on a month by month scenario, but what is the Total Cost of Ownership (TCO)?
On-premise solutions are solid choices traditionally, but they suffer from several concerns. You have a higher initial cost for a lower maintenance cost. You also take ownership of the risk when a drive pops or a surge happens. When the site’s down (power, internet, etc.), your backup solution is too. Some cloud solutions can be rigged to get a VM or at least file-share running elsewhere to limp along.
Hybrid solutions combine the benefits of an on-premise solution with a cloud solution. The cost is primarily financial. You have to maintain an on-premise device, the service for it, and a cloud solution. The major benefit is that you provide a substantially better backup solution with more flexibility and redundancy.
Which Is Better: Cloud, On-Premise, or Hybrid?
Each of these solutions is different, but none of them are objectively better. The cloud solution trades local networking access for a more resilient medium. This solution also relies on an app or similar to sync, so the average ransomware attack is typically useless against the backups. A backup is a backup.
On-premise solutions are typically faster, more robust failovers, but also suffer from being physical devices onsite. If a drive pops, it’s on you to fix. If it’s vulnerable to certain attacks, ransomware may take both your client and their backup in one swoop.
Hybrid approaches get the best of both worlds, but at the cost of maintaining multiple solutions. Some vendors like Unitrends offer hardware programs to offload some of this cost, but no matter who you use, a hybrid approach is going to be more than any single approach. Not every vendor offers both either.
The best solution is the one which works the best for you and, more importantly, your client. While this seems commonsense, it requires you to know what works best for your client rather than just what works for you. Some solutions are more flexible than others, but some are definitely one-trick ponies.
What does their internet connection look like? Do they have usable hardware or is an on-premise solution an additional expense? How much data do they typically use, how much do they need, and how much is it worth to ensure access? There’s a continuous cost-benefit analysis which needs to be done to decide the best solution. To top it all off, how much is it worth to them, and you, to learn to deal with this solution?
What Are the Big Pitfalls Between On-Premise and Cloud Solutions?
Hybrid solutions round off the problems of either by buying their way out, but what is the real difference between the individual pieces? What gotchas are there for on-premise versus the cloud? Each solution is different, but there are inherent differences between the cloud and on-premise solutions.
What bandwidth is available? The more bandwidth the site has, the more practical a cloud solution is. One thing many backup specialists forget about is the cost in terms of time and money to restore a backup. Slow uploads with slow changes can mask the cost of a slow download.
How much data is required to function? The more data is necessary the more an on-premise solution makes sense. You can physically pull a hard drive but you can’t really pull a drive out of the cloud. Some businesses build off of terabytes for their day-to-day operations, others only need a little bit. Where is your client?
Money is another concern. A business can’t function without IT, but they’ll cut corners unless it hurts enough. IT is viewed as an expense to most businesses. Can you move them if the cloud is the wrong answer for backups but it’s cheaper?
While each of these factors has an effect, what do you do when a client is a mismatch of bad for both solutions? A combination of a site with slow bandwidth, bad infrastructure, security issues, low budget, and a high amount of data is not going to fit either an on-premise or cloud solution. While this sounds like a nightmare, they still want to eat their cake and have it too. How you plan for this can be the difference between signing a client and losing them.
How Do You Sell Backups?
Very few people realize the value of a backup until they need one. Techs tend to experience this earlier than many career paths, but there are lucky people who’ve never truly felt this lesson. You don’t realize the value of an eraser until you make a mistake.
A client which has lucked out on every disaster will be harder to sell to. The desire for a backup comes from the understanding of what happens without data or an encounter with the solution itself. You don’t need a client to experience disaster to know they need backups (but it helps).
Ransomware runs rampant waiting for the next vulnerability and bit of luck to stick. Hard drives, tapes, etc. die with age. Even the wrong user can break everything if they hit the wrong thing. You need to do is make your client aware of this risk and how it impacts them.
Very few businesses say no to a backup after their first disaster. The problem is that very few stay in business after their first major disaster. We aren’t dealing with fear mongering; we’re looking to prevent catastrophic risk.
It’s one thing to not have insurance for a car you own, it’s a different thing to drive without it. When your client tries to operate without backups, they’re driving their employees and clients around without insurance. You’ll be fine until you aren’t. The more data you need, the worse off you are in a crash.
Backups aren’t just a good idea; they’re insurance against the technical unknown in many respects. Sell your clients on the benefits of backups by understanding what makes their business work. IT isn’t a service, it’s a utility. How do you keep your client from destroying themselves without breaking the bank?
Meet Lance Keltner of UNI Computers!
Tell us a little about your MSP…
UNI Computers was established in 1993 as a computer repair store in Lawrence KS. I took over ownership in 2006 after working there for 7 years. At that point, business managed services was a very small part of the business, but I knew it would be the future and where I needed to focus growth. I continued to put time and effort into growing the business services side of the company and today it accounts for more than half of our total revenue.
How long have you been a member of The 20?
We joined The 20 in 2018 and are a bit past 2 years of being a member.
Why did your MSP originally look to partner with The 20?
The selling point for me was two fold and equal in importance: #1 was the pre-curated stack of tools and security with the foundation already set and process in place to use, sell, and manage it. #2 was the community. I know enough to know what I don’t know, and having a large community of people just like me with all different experiences and skillsets is ultra-valuable. Whenever I need an answer or solution to something, chances are someone has it and already knows it works.
Tell us about the biggest change in your business since joining The 20.
The biggest change for us is having a solid process that I didn’t have to invent from the ground up over the course of years that’s already proven to work. I sell with supreme confidence backed not only by me, but also vetted by scores of other businesses around the country doing it the same way as I do, every day.
What do you like most about being a member of The 20?
What I like most is definitely the community. I’ve formed life-long friendships here, which is not something I always do easily. Everyone is here to help out. No one is afraid of someone else stealing their stuff. That’s rare in the world where everyone generally keeps their cards close to the vest. I also like that if I need to get top leadership of The 20 on the phone for a call, it’s easy to do, and they are ready and willing to help with anything. Our suggestions are taken seriously and more often than not brought into practice and used. We are part of the process that makes The 20 better today than it was yesterday.
What do you think is the most important quality necessary for success?
The biggest quality for success is the willingness to change and adapt when it’s shown that you can do something better than you were doing it previously.
What are your biggest business challenges?
My biggest challenges personally are marketing and sales, which The 20 has helped with immensely but also the community and the people I have met have helped equally as much. The collaboration I’ve been able to do with other members has been priceless.
What are your areas of focus for 2020?
My biggest areas of focus are getting in front of prospects and keeping the pipeline full. COVID brought about a lot of instant change, but we were fortunate enough that our base of clientele was very stable and so we haven’t suffered like some MSPs have. Reaching new customers and bringing them the security and support they need has definitely been more challenging, and is the key area I’m working on as it dictates our overall growth.
What advice would you share with an MSP looking to scale their business?
Join The 20! Seriously. Tim says the three most important things you can do are 1. Lead Gen, 2. Sales, 3. Scale. That’s what The 20 is built on and what its focus is. If joining isn’t possible, then those three things are still what you have to do, anyway you can. They will decide how successful your MSP can be. Period. I’ve doubled my MRR since joining The 20. This is the way.
What book are you currently reading?
I am currently in a few different books, which are all great: The 4hr Work Week – Tim Ferris, Traffic Secrets – Russell Brunson, Building a StoryBrand – Donald Miller.
Favorite blogs / podcasts
I haven’t been much of a podcast guy as I usually like reading more, so for blogs/sites it would be:
1. The 20’s Teams community!
2. Chris Wiser’s marketing program communities
3. Cyware’s security daily email
4. Recorded Future’s daily email
Interested in becoming a member like UNI Computers? Click here for more information!