
by Sage Driskell
Common Phishing Techniques
“Microsoft Support” | This is an extremely common scheme that many people fall for. Someone receives a call or email from “Microsoft” saying they’re compromised, and the “technician” helps the user allow them to connect to the machine in order to compromise their system. A lot of times, they leave behind malware or other remote access tools which they can use to later harvest information. They also typically charge for their “assistance” and collect data either via an invoice or on the phone.
Bank Emails | This is the most well-known phishing attempt. You get an email “from your financial institution” and the domain is usually close to the original, but always a bit suspect. These pages are identical to the bank’s page as well. The easiest way to avoid these is to always log in to the bank site directly rather than doing anything from an unknown communication from them unless you specifically know an email is coming (e.g. password reset).
IRS Emails | As we know, the IRS is almost impossible to work with, so they won’t make your life easy to just call you and square everything away over the phone or via email. These types of phishing attempts typically involve “the IRS” reaching out to you about a “tax issue” and they’re glad to either collect information (including your social) to “process your case”, or in some cases, they’ll take money to help “pay off the owed sum today only”.
Compromised Service Emails | These are a “warning” from a provider that “the service may have been compromised” and they need your details to continue. The login page is usually either really good or else really obviously bad. There is very rarely a middle ground on these. They will sometimes include a specific email or form to make it easier.
Fake Invoices | This is a fake invoice requesting money for some service. These are commonly used to target companies. The invoices are usually extremely generic, may or may not ask for personal details, and target companies where it is easy to miss a small expense.
419 Scam | These used to just be scams, but they’ve grown in some ways. The goal is to get both your money and your identity. These will typically be a business venture or something, but unlike classic 419 scams, they don’t just start asking for $10k for your $10mil “which is stuck in processing and needs the money to be released, Western Union only please!” These will start out as small investment opportunities or similar which may actually show some signs of legitimacy before the big hit.
Spear Phishing | You know that cool flash drive or CD you found in the parking lot near your sensitive workplace? It may be infected with malware or spyware to try and infiltrate your environment. That is the most common spear phishing technique at present. It’s literally just a cool looking piece of media loaded with all sorts of malware.
Signs It’s a Phishing Email
The first thing to look for in any questionable email is this: is this someone I do business with? If you don’t have an account, you obviously have no business receiving their email except as spam. Another thing to look for is the trends of the institution. What I mean by this is, if you’re dealing with a bank, they don’t want you to email them a form. Look for obvious grammar and spelling mistakes. These can be telltale sign that something is amiss. Most financial institutions and similarly private types of institutions want you to sign in and fill it out on their page and will almost always have an internal way to do this from their login from an internal messaging portal or similar. If in doubt, log in directly and look and see if this is a legitimate communication. If it is, you may still be compromised and should still take caution.
Another thing to look at is the domain. Does the domain match the exact one you use for your bank or similar? The names may be very close, but they tend to have some minor issue with them or will redirect through something else. Just because it looks right doesn’t mean it is. You can also check the SSL certificate to see if it is legitimate or not, but that’s a bit more complicated.
Any service which is reaching out can also be called or otherwise contacted to verify the legitimacy of a claim. No one has time for every communication, but anything which looks pressing may be worth trying to communicate with the vendor or service over. I personally just ignore everything unless I get officially contacted about it or know it’s coming.
Another strategy I use is different email accounts tied to specific services. I work with one bank with one account and another bank with a different account. I know I can only receive one banks communication on a specific email, so anything on the other email is obviously a trick. Using email accounts only for specific accounts (and literally nothing else) helps well since you have a lower chance of the email being leaked, but this does require more effort and upkeep.
Further Signs
For more advanced users, you can look at the email headers (to do this in Outlook, see: https://www.technipages.com/outlook-view-message-headers). If you see something like the following message:
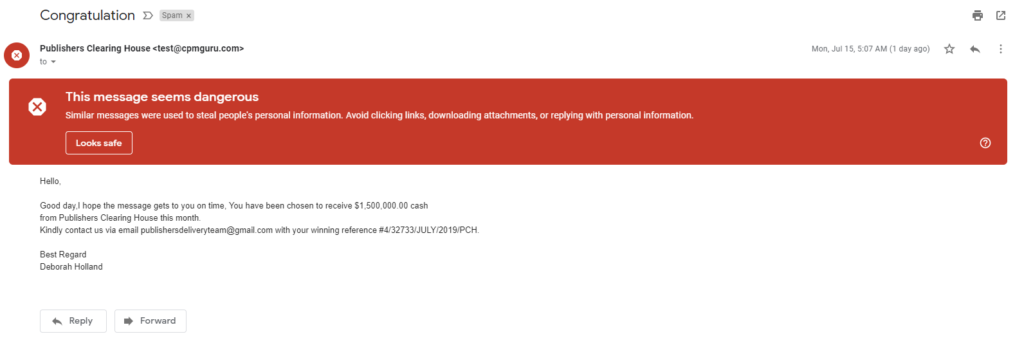
We can see that this is coming from a [email protected] — which I have no idea what that is — and the email to contact is [email protected]. The domains do not match and neither of these have anything to do with Publisher’s Clearing House. I could not find a specific phishing email in my mailbox with forged headers, but see something like: https://www.alienvault.com/blogs/security-essentials/how-hackers-manipulate-email-to-defraud-you-and-your-customers for an example of what to look for. There are legitimate uses for a “forged” header, but this is typically for bulk mailers and similar, and is rare with official communication.
Another thing to look at is the TLD. If the TLD is foreign for something which is US only, you can almost guarantee the email is a phishing attempt. If the TLD doesn’t match the actual company TLD, then you probably have an issue too. Apple.net is not Apple.com. Tech giants like Apple will tend to nail down sister domains, but smaller companies usually don’t have the resources to do this.
Another trick is to copy and paste the domain from the email into something like: https://www.diffchecker.com/ and then copy the domain from the email. You might get something like:
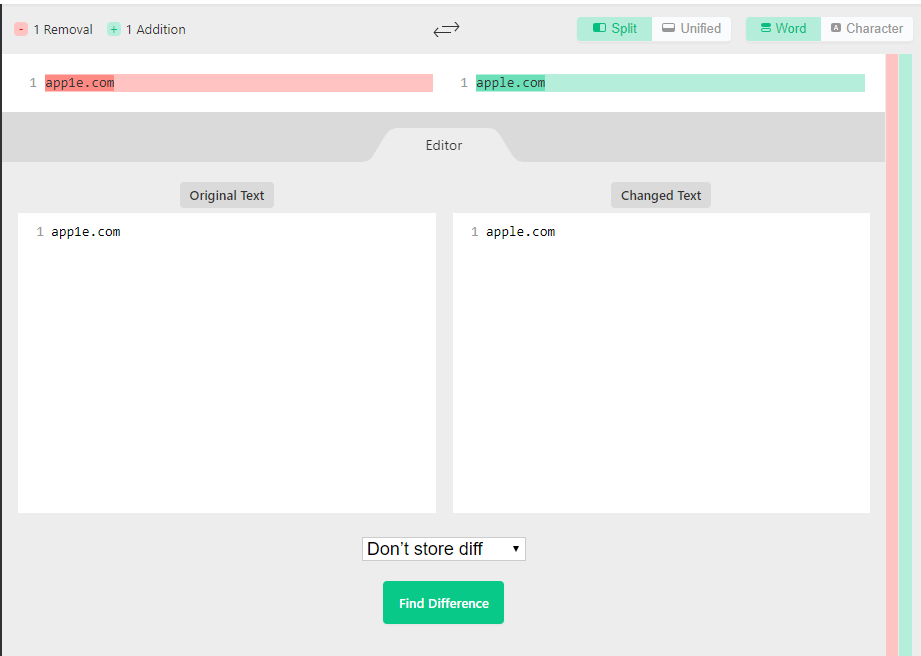
This is obviously a phishing attempt since the domains do not match. With the right font, these are somewhat obvious, but a common tactic is to use Unicode characters or similar characters in another language in order to get around this sort of limitation. This technique helps weed out some of the more obvious tricks, but you should still check the headers.
How The 20’s Security Offerings Mitigate Phishing
Vipre Email Security
Vipre Email Security is the new name for Fusemail. This service blocks both malware and phishing at the source. You don’t need to worry about a user clicking on malware or getting phished if they don’t even see it in the first place. Setup is easy and convenient and is pretty much ready to go (that is, no crazy lists or other hoops like some services) once the initial setup is complete. No solution is perfect however, so training and combination with a tool like OpenDNS makes this tool substantially more powerful. Vipre Email Security gives you the control to throttle scams and phishing attempts in order to keep your clients safe.
OpenDNS
OpenDNS isn’t typically thought of as a way to mitigate phishing attempts, but it works great against fake portals. OpenDNS is easily configurable and scalable for agents at your client’s sites. It prevents the few phishing attempts which get by from being as impactful. There are caveats to this however, but we have seen many tickets from confused users unable to submit their sensitive data to scammers. OpenDNS is flexible and easy to deploy to individual agents or across a network. From a domain environment to workers in the field, OpenDNS has an option to get you covered.
Deep Instinct and Huntress
Deep Instinct and Huntress help prevent and remove compromises from the inside which can lead to legitimate emails becoming weaponized into near impossible to discern phishing from legitimate accounts. By preventing infections, you prevent data leakage and lock down on threats which may threaten your client’s systems with ransomware as well as keyloggers. Deep Instinct and Huntress are like Yin and Yang. Deep Instinct is the prevention, Huntress is the remediation. Find exploits on new clients and help lock them down preventing more seemingly legitimate, internal threats which lead to phishing and worse.
To learn more about The 20 and how we can help your business, be sure to check us out here!


