Meet Allan Sivils, CEO of Sivils IT Consulting!
Tell us a little about your MSP…
Sivils IT Consulting is located in Virginia Beach, VA. We were established in 2014 after I spent 15 years managing enterprise IT operations. I wanted to create a niche business that focused strictly on partnering with our clients’ IT operations, and not selling software or hardware. We focus on building true partnerships with our clients that allow us to advocate for their business growth.
How long have you been a member of The 20?
We joined in December 2019!
Why did your MSP originally look to partner with The 20?
A couple of reasons – The 20’s model is very similar to what we have been building since we started our business; to focus on being the best “Managed IT Department” for our clients. So, it made perfect sense from a partnership standpoint. Second, we have clients on both coasts, and being a part of The 20 gives us the resources that we need in order to serve clients across the United States. This allows us to scale faster, while not sacrificing the quality that our clients should expect. Lastly, the shared expertise of being a member alongside other top MSP’s allows us to work together to bring the best solutions to our clients.
Tell us about the biggest change in your business since joining The 20.
We do not feel limited by how much we can scale our business by being a member of The 20.
What do you like most about being a member of The 20?
The network of being a member. Being part of such a large community has already helped us since joining in December operationally. We’ve been able to provide onsite resources to our clients that are thousands of miles away, and have these resources follow the same processes we do internally. We’ve been able to implement better technical solutions and processes that have helped us internally to service our clients.
What do you think is the most important quality necessary for success?
Relationships. Both within our MSP community, our vendors, and especially our clients.
What are your biggest business challenges?
Managing the ebb and flow of IT projects around our clients growth – while we do our best to ensure that we can schedule to meet expectations, sometimes the volume of projects needed at one time can be difficult to manage. Also, sometimes projects require a wide range of very specific expertise. Being a member of The 20, this is quickly becoming less of a challenge.
What are your areas of focus for 2020?
Microsoft Azure, Windows WVD and Nerdio. We see that these have a huge operational advantage and efficiency versus having workloads onsite. It also helps us scale our clients faster, while ensuring their business continues to have the highest availability for their operations.
What advice would you share with an MSP looking to scale their business?
Stay focused on the relationships I mentioned above and being the IT Department advocate. Unfortunately, due to the nature of the business, with a lot of us being engineers that get too focused on the details, leverage your fellow partners/vendors instead of trying to take the entire pie for yourself. Follow this up by a repeatable IT operational standard and processes that will be clear and focused for your team to support and, most importantly; stable, secure, and protected for your client.
What book are you currently reading?
I travel a lot, so by “reading…” that really means “audio book” for me. This would be Traction by Gino Wickman. I’m actually listening to it again! I will listen to audio books that I have enjoyed, multiple times — that is — if I find the information extremely valuable.
Favorite blogs / podcasts
Honestly, I don’t have any. I spend so much time investigating, reviewing, testing, and reading about various IT solutions and methods. I guess I would say, I read “the internet.”
Interested in becoming a member? Click here for more information!
Baselines: What’s in your IT estate?
Heroes get business. When a customer thinks of you as a hero, they become your advocate. That same customer will run out into their network and let everyone know that you are the hero everyone needs. That same customer will also come back to you with future needs. All thanks to you informing them of Crayon Baselines.
Crayon Baselines is the beginning of the journey to optimization. The software compliance path begins with a Microsoft Baseline and ends with Agreement Optimization. Packaged separately, they work hand in hand so you can earn revenue, valuable customer insights, and reduce churn, which leads you to a big pile of cash. The Baseline is the gateway.
What is the Baseline, and how does it drive attach?
Through a Microsoft Baseline, Crayon offers your customers visibility into their entire Microsoft Software Estate. Foundationally, the Baseline shows your customer’s license entitlement vs. usage. 83% of the time, customer license utilization is imbalanced. As a Crayon partner, you will get to play the hero when you deliver data that demonstrates the sky is falling. You don your cape by delivering a comprehensive entitlement report to position the path forward.
If Baselines present the path to the solution, Agreement Optimization is the solution. In Agreement Optimization, Crayon will look at the Baselines, determine future needs, and make recommendations for optimizing the license agreement. Crayon will give you the playbook and sit side by side with you, ensuring the license agreement drives savings and growth for your customer. Together with Crayon and The 20, you walk away, looking like the hero.
#CRAYONBASELINES
Join Crayon March 4th at 10am CST for a Leadership Webinar featuring John Rex former CFO of Microsoft. Your participation is encouraged; so, please come with questions!
Meet Lee Mash, Business Development Manager
Today we turn the spotlight on Lee Mash. Lee has quickly become a tremendous asset to the Sales team and The 20.
What do you do here at The 20?
I’m the Business Development Manager, which means I’m in charge of member recruitment. I search for potential MSPs to see if they’re the right fit to join The 20.
Describe The 20 in three words…
Revolutionary, Teamwork, Unique.
As a kid, what did you want to be when you grew up?
I wanted to be an astronaut.
What’s the most challenging thing about your job?
Finding MSPs that REALLY are open to change. Change is difficult, and most people say they’re committed to change — but when it comes down to it, they don’t want to leave their comfort zone. Stepping out of your comfort zone is the only way you’ll grow and excel.
What do you consider your greatest achievement?
Finishing my training and being accepted into the Elite Nahal infantry brigade of Israeli Defense Forces was my greatest life achievement. Our beret march was around 100 miles and I carried almost 100 pounds of gear. Climbing up Masada in full combat gear; carrying the stretcher while watching the sunrise and knowing I finished this trek was breathtaking. A task that I originally thought was impossible, became possible and that’s when I realized YOU can be the greatest barrier to your own success.
What do you think is the most important quality necessary for success?
Self-discipline.
What do you like most about The 20?
The 20 gives every MSP the chance to grow, no matter their size or where they’re at in their business plan. If they have the will and motivation to grow, The 20 enables them to unlock their true potential.
What do you like to do in your spare time? / What are your hobbies?
In my spare time I enjoy working out, playing ice hockey, hanging out with friends, reading, laying on the beach and traveling.
Where are you going on your next vacation?
I am going to Israel, Egypt, and Jordan in May!
What’s your top life hack?
Wake up before sunrise and you’ll be exponentially more productive! I guarantee it!
Interested in working with Lee at The 20? We’re hiring! Check out our Careers page for more info.
Tim Conkle Recognized on CRN’s 2020 Channel Chiefs List
View the full release here
The 20, leading MSP consortium, announced today that CRN®, a brand of The Channel Company, has named Tim Conkle to its 2020 list of Channel Chiefs. This annual list recognizes the top vendor executives who continually demonstrate exemplary leadership, influence, innovation, and growth for the IT channel.
Tim Conkle holds over 30 years of entrepreneurial success in the Information Technology and Services sector. As a leading voice in the Managed IT Service Provider space, Tim is dedicated to developing simple, solid IT solutions for SMB clients and MSPs (Managed Service Providers) across the nation. His notoriously energetic nature, along with his deep-rooted passion for technology, has helped him forge solid customer relationships built on trust, dependability, and service.
As CEO of The 20, Conkle is the driving force behind a business revolutionizing the IT industry. By utilizing a proven multi-million dollar sales model and an execution framework that he developed, Tim helps MSPs attain profitability and success. Through The 20’s business model, Tim has advised hundreds of MSPs in sales and operations, resulting in catastrophic revenue generation and millions of dollars in savings from process improvements and single-funnel vendor access.
“I am honored to be recognized as a 2020 Channel Chief alongside a roster of remarkable individuals,” said Conkle. “This past year has been an incredible journey with many big developments for The 20, and I am looking forward to all we have in store for 2020.”
CRN’s 2020 Channel Chiefs list honors the distinguished leaders who have influenced the IT channel with cutting-edge strategies and partnerships.
The 2020 Channel Chiefs have shown outstanding commitment, an ability to lead, and a passion for progress within the channel through their partner programs. The Channel Chief honorees were chosen by the CRN editorial staff for their dedication, industry prestige, and exceptional accomplishments in driving the channel agenda and evangelizing the importance of channel partnerships.
“The IT channel is undergoing constant evolution to meet customer demands and changing business environments,” said Bob Skelley, CEO of The Channel Company. “CRN’s Channel Chiefs work tirelessly, leading the industry forward through superior partner programs and strategies with a focus on helping solution providers transform and grow. Our team here at The Channel Company congratulates these outstanding individuals for their dedication to the channel.”
CRN’s 2020 Channel Chiefs list will be featured in the February 2020 issue of CRN Magazine and online at www.CRN.com/ChannelChiefs.
About The 20
The 20 is an exclusive business development group for Managed Service Providers (MSPs) aimed at dominating and revolutionizing the IT industry with its standardized all-in-one approach. The 20’s robust RMM, PSA, and documentation platform ensures superior service for MSP clients utilizing their completely US-based Help Desk and Network Operations Center. Extending beyond cutting-edge tools and processes, The 20 touts a proven sales model, a community of industry leaders, and ultimate scalability. For more information, visit: www.the20.com or go to LinkedIn, Twitter or Facebook.
About The Channel Company
The Channel Company enables breakthrough IT channel performance with our dominant media, engaging events, expert consulting and education, and innovative marketing services and platforms. As the channel catalyst, we connect and empower technology suppliers, solution providers and end users. Backed by more than 30 years of unequalled channel experience, we draw from our deep knowledge to envision innovative new solutions for ever-evolving challenges in the technology marketplace. www.thechannelcompany.com
An MSP’s Guide to Surviving Phishing in 2020
Phishing is a hot topic for security in 2020. Hackers are getting smarter and security services are struggling to keep up with some of the new, highly targeted campaigns. What do you do when the user overrides every protection in place falling prey to a highly targeted phishing campaign? What does their employee do when it’s supposedly the CEO calling?
A new trend making the news is deciding who holds the liability in the event of phishing. The core argument of the suit boils down to: “[T]he MSP didn’t provide the necessary service or training required to stop the crime.” How much is on the company and how much is on the Managed Service Provider (MSP)? This whole suit will set a precedent one way or another for MSPs.
Avoiding Liability
How do you plan your security stack to avoid phishing? Do you focus on only security or do you use training as well? Do you keep your clients fully up to date against new threats? Do you cut down on allowed software at the site? How you answer and understand each of these affects how the ruling on this case will affect you.
With new threats on the black market and the continued improvement in phishing and other targeted attack methods, where exactly does the line between corporate culture and best faith from the MSP lie? This case may determine that, but this is something which needs to be worked into a contract on signing. Where does your best faith effort and their negligence begin? This can help determine your liability in an event, if any.
Let’s move on to what you can do for best practices to avoid omitting your responsibility to your client.
Shoring Up Security
A machine is 100% efficient 95% of the time. The distinction between this just being 95% is important. An ideal person will be 95% efficient 100% of the time in an ideal position. This also works out to 95%. Despite the fact our numbers work out the same, the machine never makes mistakes on the same class of problem. It has problems it just can’t solve though.
A well placed employee will be the opposite of the machine in that they can solve any problem in their arena, but will make minor mistakes randomly. The goal is for these to be far and few between, but a real life person being right 90% of the time is amazing, 95% is almost unheard of. The magic comes from combining the two, you remove the chance of the low hanging fruit from being exploited, but use human efficiency on the harder problems. You won’t get 100%, but you’ll get 99% with a little bit of training and a good security setup.
Digging Into the Technical Side of Phishing
Target how phishing works. Target the human elements of cybersecurity first for assigning technology. Where do most phishing attempts originate? They come from email and websites.
Tools like OpenDNS or Vipre Mail provide a way to stop known phishing domains and suspicious emails. OpenDNS blocks questionable domains and provides the chance to put in custom error messages. Vipre Mail stops spam emails and provides reports to companies. Combine the tool with a way to address the human causes of these problems. A tool which doesn’t tell you what happened and why is useless.
Do you employ MFA to make sure that a compromised password is a minor concern? Do you know when a password is compromised without a mess ensuing? Do you monitor the dark web for compromised information? Make sure your client takes measures for themselves to reduce technical attacks.
Training Your Users
If the average user acted like the average power user, antivirus would almost be pointless. Spam and phishing would have to become significantly smarter or it would just disappear. It just takes one employee clicking the wrong link to compromise the entire company. Have you had the first painful conversation about the fact that not everything on the internet is true with the weakest links? It’s painful, but often necessary.
“An ounce of cure is worth a pound of cure,” rings truer than ever with modern phishing. I go months without spam hitting my inbox, but when it does, it’s usually extremely well done. IRS.com wants you to report your social security number and provide a good email to verify if you have been compromised or not. What do you do?
Do you inspect the certificate first or look at the form and see if there is some kind of redirect? Or do you see the domain first? The average user doesn’t care about the difference between TLD’s and why IRS.gov is more believable than IRS.info. How much pain do you save explaining that you shouldn’t fill in information for Bank of America when your company only uses Chase?
Better Verification
What do you do if someone calls asking your department to fulfill an invoice? What do your users do? If you hear a familiar voice on the other end, you’re probably going to comply. The problem is that now we have deepfakes which can emulate a person. Are they having a bad day or are they actually a computer? You won’t know until you comply (or don’t).
Most extremely large companies employ some kind of verification system. We built our own system to prevent these sorts of issues and make it more accessible for our clients. How do you make sure a user hasn’t been fired minutes ago and is calling to get access to what they shouldn’t have access to? You don’t unless you can check.
Moving Forward
While the lawsuit hasn’t quite taken it’s course as of writing, either way, you need to make sure you solve your client’s issues. Where do you draw the line? If John in finance is allowed to use “password123”, what do you do when they get hacked? Who’s fault is it?
You have to have a plan, and you have to have a way to address any of the client’s bad security practices. Do you support them regardless, address the problem, or refuse service? Support means the potential of liability, addressing the problem depends on the client, refusing service means losing money. What’s the right answer?
There really isn’t one… yet. The best you can do is take every step towards securing your client. Focus on technology and training as well as you can and you reduce the attack surface. No matter the ruling, you should be riding your client and pushing them towards success one way or another. Make your life and their’s easier with technology and tools like ID 20/20 along with training.

by Sage Driskell
Meet Mark Elliott, CEO of 3i International!
Tell us a little about your MSP…
3i International is located in Houston, TX. We have 25 employees and have provided expert IT services since the year 2000. We are awesome at security and managed services, and our mission is to help people be their best by making technology easy and secure. We have a great team and have a lot of fun every day!
How long have you been a member of The 20?
3i International joined The 20 in December of 2018.
Why did your MSP originally look to partner with The 20?
Great question, this is a two-part answer for us. First, we were looking to move upmarket to larger clients and wanted a way to deliver services on a national level where we did not lose control of our customer or have degradation in support by hiring one-off boots on the ground. Secondly, we were having challenges scaling the business, and it kept leading to service delivery issues. Before The 20, we had a great company with talented engineers, and our clients loved our support and personal touch. At our size, we did not have separate teams for the helpdesk and onsite engineers. Every engineer had a seat in the call center, and when needed, they would be sent onsite. This methodology worked well as long as we did not grow. Every time we had major projects or a large new client onboarding, we would have to move resources from the call center to install equipment or onboard new seats. As soon as we reallocated resources from our call center, the level of service that our clients had become accustomed to would fall. We would then move some resources from the field back to call center only to have project deliver suffer. We found our company stuck on a staffing teeter-totter with happy and then unhappy clients. The 20 gave us the ability to truly separate our call center from the onsite and project team, which has been a Godsend. We now have happy clients all the time, not just in between waves of growth.
Tell us about the biggest change in your business since joining The 20.
We are closing more new MRR deals every month with the 20 offering and pitch. Our pipeline has grown with higher monthly recurring opportunities than we had before. The 20’s footprint has allowed us to focus on larger companies with multiple locations in different cities. We have found a real need here as an internal IT department with 500 employees cannot successfully support 20 locations with a couple of engineers. Our customer satisfaction with project delivery is through the roof. The 20’s call center handles the majority of our tickets, so we were able to shift our team around and create a dedicated team focused solely on project delivery. During our growth, we can now provide great support from the call center, our local onsite team, and the project team.
What do you like most about being a member of The 20?
The community is awesome, from weekly accountability calls with other members, the ability to message nationally on Microsoft Teams to find an answer to a tough question, the comradery at quarterly training meetings. It just a strong group of like-minded individuals with 1000’s of years of experience all fighting to make a difference in the lives of their customers and their families. The services The 20 provides encompass most of what an IT company needs to succeed. It is a great offering of tools at a fair price. We were concerned about what our customers would say about the changes, but our customer satisfaction continues to increase since becoming a member.
What do you think is the most important quality necessary for success?
I don’t. I think this question could be answered ten different ways by ten people, and no one would be wrong. You might hear answers like grit, ambition, courage, commitment, willpower, drive, integrity, and on and on, you get my point. So why is it that sometimes you see individuals with these traits fall short of their full potential? I have been at this game for 25 years now, and I know that I possess all of the traits I just listed above. I am moderately successful, debt-free, and can retire comfortably in a few more years. By national standards, I’m in the top 1%, but by no means do I have a yacht or private aircraft. My journey to this point has been a dog fight in a highly competitive market. So, I think great success takes more than character traits as they are table steaks in today’s business climate. I feel to blow it out of the water truly you have to be first, better, or different. I feel the opportunity The 20 has afforded my company compliments my character traits by creating a differentiation that allows me to reach my full potential.
What are your biggest business challenges?
Last year we spent time identifying our weaknesses and threats. Now, last year’s challenges are this year’s opportunities as we have prioritized what we will be fixing and implementing during this calendar year. This year we are working on increasing outbound lead generation to 50 leads per month, implementing an employee training program around culture and function, standardizing our QBR methodology, and executing on a new inbound digital marketing strategy.
What are your areas of focus for 2020?
We are an EOS company, so we will continue to implement and improve our use of the traction tools set. From a top-line perspective, we are focused on growing monthly recurring revenue in the healthcare, legal, AEC, manufacturing, and energy verticals.
What advice would you share with an MSP looking to scale their business?
Identify what’s holding you back, and if you’re willing to fix it, find a business coach or organization with the skill set to help you solve your challenges and hold you accountable. Don’t be afraid to partner with The 20. It is one of the best decisions we have made for our business and the people we support.
What book are you currently reading?
I recently just finished setting my personal goals for 2020, which includes a list of 36 books. Here are the three that I am currently reading in January:
1. The Big Leap – Gay Hendricks. This book is about removing upper limiting beliefs in your personal and business life that keep you from reaching your full potential.
2. The Road Less Stupid – Keith Cunningham. I am reading this book for the second time. Incredible lessons that are easily digestible like fatherly advice.
3. The First 90 Days, Updated and Expanded: Proven Strategies for Getting Up to Speed Faster and Smarter – Michael Watkins
Favorite blogs / podcasts
Chris Voss – The Negotiation Edge
Guy Raz – How I Built This
Interested in becoming a member? Click here for more information!
Well that’s a wrap on another successful Quarterly meeting with our members!
Winter Quarterly was held at our offices at Legacy Central in Plano on January 16th and 17th, and we had an incredible time with all of you.
You’ve got to win somewhere before you can win everywhere.
– Joseph Landes of Nerdio
Our first day was entirely dedicated to in-depth training sessions by Nerdio, CloudJumper and Crayon. Each company discussed how to sell, calculate and implement Azure. The day concluded with a happy hour. It was 2 hours of games, music and good times spent with our 20 family!
Day 2 kicked off with Tim Conkle who went over with our members the best way to sell cloud and how to package it with our other software platforms. Everyone is moving more away from hardware and towards cloud.
So much was learned, and so much fun was had – there’s nothing we look forward to more than when we have our partners in town, and in the same room. It’s a tremendous energy, and we’re always sad when it ends!
If you have any questions about future Quarterly events, please contact us today to learn more about The 20! We’d love for you to be a part of our Spring Quarterly in May!
And don’t forget to sign up for our MSP Sales Academy going on next month!

Tim clowning around before start time!

Panel discussion lead by CIO Jeff Griffin, CTO Jonathan Blakey, SVP of Sales Roxann Sawyers, and COO Ciera Cole.
How CVE-2020-0601 the Chain of Fools / Curveball / NSACrypt Attack Affects You

by Sage Driskell
CVE-2020-0601 was announced to the public on January 14, 2020, as a warning about the Cryptographic API in Windows 10 and Server 2019 (there are rumors of Server 2016, but we have not explicitly verified this) and with a patch to resolve the issue on affected machines. As of reporting, there were no known attacks using this attack vector in the wild. Since then, the vulnerability has gotten a name (actually a few names), and some researchers have released proofs of concept.
If you want to validate a system and whether it’s susceptible or not, go to: this test.
What Is It?
CVE-2020-0601 is known by several names now. There’s Curveball and NSACrypt, as well as Chain of Fools. There are several names in circulation, but they all point to the same flaw. Let’s go over what the exploit is first.
Per Microsoft:
A spoofing vulnerability exists in the way Windows CryptoAPI (Crypt32.dll) validates Elliptic Curve Cryptography (ECC) certificates.
An attacker could exploit the vulnerability by using a spoofed code-signing certificate to sign a malicious executable, making it appear the file was from a trusted, legitimate source. The user would have no way of knowing the file was malicious, because the digital signature would appear to be from a trusted provider.
A successful exploit could also allow the attacker to conduct man-in-the-middle attacks and decrypt confidential information on user connections to the affected software.
The security update addresses the vulnerability by ensuring that Windows CryptoAPI completely validates ECC certificates.
If we dig a little deeper with newer information, we find the following from cert.org:
The Microsoft Windows CryptoAPI, which is provided by Crypt32.dll, fails to validate ECC certificates in a way that properly leverages the protections that ECC cryptography should provide. As a result, an attacker may be able to craft a certificate that appears to have the ability to be traced to a trusted root certificate authority.
Any software, including third-party non-Microsoft software, that relies on the Windows CertGetCertificateChain() function to determine if an X.509 certificate can be traced to a trusted root CA may incorrectly determine the trustworthiness of a certificate chain.
Microsoft Windows versions that support certificates with ECC keys that specify parameters are affected. This includes Windows 10 as well as Windows Server 2016 and 2019. Windows 8.1 and prior, as well as the Server 2012 R2 and prior counterparts, do not support ECC keys with parameters. For this reason, such certificates that attempt to exploit this vulnerability are inherently untrusted by older Windows versions.
So, a core function in Windows 10 based OSes for determining the key of an ECC cert which has been generated can’t be trusted until this patch is applied. This does not affect older Windows OSes though.
What Is Elliptic-Curve Cryptography (ECC)?
Elliptic-Curve Cryptography (ECC), or ECC is a form of cryptography using a mathematically generated curve algorithm instead of the traditional key method. In short, we’re passing some variables to build a key to an algorithm rather than just passing a big key to do our encryption and decryption (obviously, this is a gross simplification). This means that we use less complexity for stronger encryption (theoretically).
The basis of ECC is the following equation: y2 = x3 + ax + b
If we graph an arbitrary example of this, say: y2 = x3 – 5x + 10, we get:
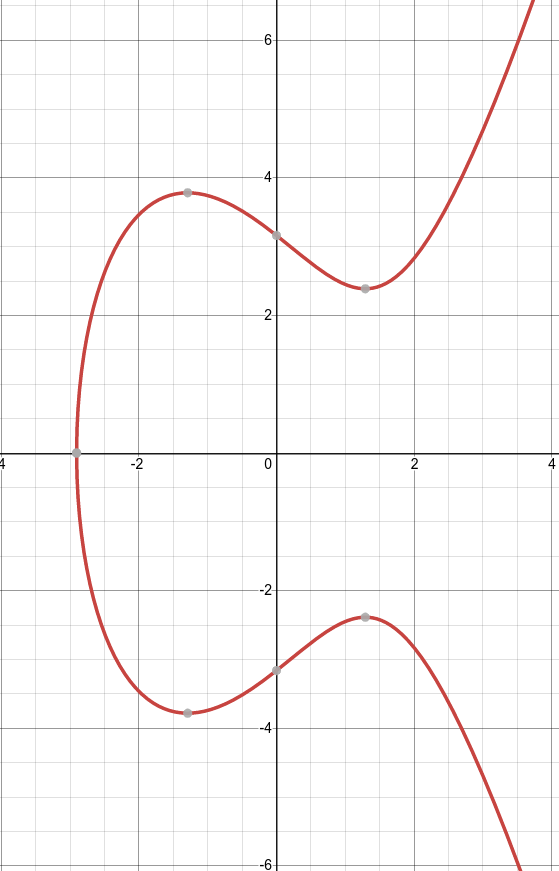
A diagram of an ECC curve for: y^2 = x^3 – 5x +10
The way the ECC algorithm works is we draw a line through parts of the curve and let it “bounce” per a known algorithm. We know it will “ricochet” a certain way and with some other conditions we can get a starting and an ending spot where it crosses the curve and bounces across. These numbers will be meaningful with a little data, but almost useless otherwise. There are a lot of equations which will get you the same algorithmic result for a few points, but if you don’t know the parameters, you don’t know the underlying pieces that make up our “key”. This means a smaller key for a harder problem for all intents and purposes.
We won’t really get any further into the math, but basically, as long as we verify all of our points and all of the variables, we’re safe.
Throwing a Curveball
The problem is, for whatever reason, Crypt32.dll doesn’t verify this correctly on certain Windows 10 and Server 2019 builds. One theory is that it’s failing to verify the base point in the equation and is assuming everything is kosher on the math checking out otherwise. Hopefully there is a bit more to this vulnerability, but either way, arbitrary ECC certificates are vulnerable without this patch on certain versions of Windows.
The issue is we’re (almost definitely) doing the math correctly, just Microsoft has decided to take a few shortcuts which compromise the validation of arbitrary ECC algorithms. See the following for a PoC.
How Bad Is It?
It’s a bit scary that something this fundamental is broken on modern Windows, but there’s some good news, it’s really not that bad with a little common sense. You won’t see this issue with Firefox since it doesn’t rely on Cryp32.dll, and other browsers like Chrome have issued patches. Most AV solutions already block the generated certificates, including Windows Defender. A good firewall which inspects SSL certificates can block this as well. Ultimately, this threat has been blocked by most end-user products, the OS, and even theoretically at the network level (transport level in TCP/IP for those of you getting your certs). This also does not impact Windows Update as those are signed using RSA.
The threat has been sold as a huge deal, and it is when used. Fortunately, the attack is non-trivial (at the time of writing) so it requires a significant degree of effort to execute, plus there is requisite setup to pull off the attack. It’s a big deal, but so is a car crash. Drive safely and you probably won’t have an issue and you prevent what you can. At present, this threat is an implementation exploit and not a cryptographic exploit.
CVE-2020-0601: Reacting to the Threat
If you have an advanced firewall which can inspect certificate chains, apply those settings if possible (some apps require certs which are superficially suspicious looking) to stop all of the man-in-the-middle attacks related to this on the internet. Your AV should update itself to stop the other attacks in most scenarios, and if not, be sure to apply the patch for this vulnerability.
This is a good time to apply more secure firewall policies at a site and agent level if possible. This is a vulnerability with the specific implementation of the cryptography and not the math behind it. As long as the cryptography itself is sound, you are too as long as you can prevent the specific implementations from being vulnerable. When you throw on an advanced firewall setting to check this, you add a different way of interpreting the math into the equation and effectively check twice using the same thing implemented differently.
If this had affected Windows 7 or Server 2008 (R2), what would happen? There’s no support and this exploit (despite being relatively harmless with some preparation) would be a much bigger deal for a company and for administrators. Windows 10 has active support, but what if your AV vendor stopped caring as well as the primary OS vendor? This is a great chance to spearhead a forced move away from legacy OSes where possible.
Meet Misty Kaufman, Cloud Services Specialist
What do you do here at The 20?
I build and maintain strategic partnerships with vendors to better service/support our members!
Describe The 20 in three words…
Innovative, imaginative, resourceful.
As a kid, what did you want to be when you grew up?
I wanted to be a Foley Artist.
What’s the most challenging thing about your job?
Making sure communication flows internally and externally so everyone remains informed and up-to-date.
What do you consider your greatest achievement?
Giving birth to my son!
What do you think is the most important quality necessary for success?
Work ethic. And you have to care about all aspects of your job/position to be successful.
What do you like most about The 20?
The 20 has given me the ability to utilize many skills I have that are not related to my position. I have had the opportunity to bring my ideas to the forefront that have now become standard practice!
What do you like to do in your spare time? / What are your hobbies?
So many hobbies. Mostly I am a musician, but I also make jewelry, knit/weave and turn on a lathe. When I am not doing any of those, I enjoy watching movies and running AV at church.
Where are you going on your next vacation?
New Mexico — we are going to see my husband’s brother.
What’s your top life hack?
Always check your cables first!
Interested in working with Misty at The 20? We’re hiring! Check out our Careers page for more info.
What’s the Difference Between Two-Factor Authentication (2FA) and Multi-Factor Authentication (MFA)?

by Sage Driskell
All Two-Factor Authentication (2FA) is Multi-Factor Authentication (MFA), but not all MFA is 2FA. Multi-Factor Authentication works on the principle of using multiple pieces of secret information in order to verify identity. Standard usernames and passwords can be brute forced, but using a separate piece (or more) of information makes this more and more impractical. Some MFA schemes will use secret questions (effectively extra passwords), or a one time key from some kind of authentication application.
MFA and 2FA are a prerequisite for security anymore. It used to take days to guess an 8 character password, now it takes literal minutes on a $35 Raspberry Pi. Everything requires a password, and people can be lazy and recycle passwords. If a user’s password is compromised for one site, who knows what other accounts are now compromised? Even the most trivial 2FA or MFA solution can reduce the impact substantially.
How Does MFA Work?
MFA (and by extension 2FA) add a protection scheme based on knowledge, possession, or biometrics.
Knowledge
This form of authentication relies on a knowledge based challenge. This can be an extra password, a security question, or some other type of challenge. The goal here is to buy time without inconveniencing the user. By adding a separate password, an attacker has to gain access to both passwords, and avoid locking themselves out trying to do so. Some challenges will have multiple potential knowledge tests to make this more complex.
Some of the first MFA I ever worked with was through a bank. The bank had a list of 20 images which you picked from and added a description to. Each time you logged in, it would give you a subset of the images, you picked the one you had, and then it prompted you for the description. If you got it wrong 3 times, it locked the account for some period of time. My password got hacked plenty of times, but my account never did. Even something this low-tech ended up stopping dozens of potential breaches.
By having you pick the specific image first, it tested your knowledge. The prompt would then pop up no matter what was picked. This method is somewhat safe, but not foolproof by any stretch of the imagination. A single incident with a keylogger could get everything.
Possession
Possession challenges rely on the physical possession of a device or some other item. This can be a USB key or a device which generates a code. Most things people think of as 2FA are generally going to be a password based on possession of an application which generates a one-time key.
Almost everyone has something like Microsoft Authenticator or Google Authenticator on their phone for work or just general security. If someone manages to compromise your computer, they don’t necessarily get your account outside of the current session. Using a separate device to authenticate mitigates the effectiveness of a keylogger or of a very coordinated attack to gather information on a target. A user can tell someone about their first pet “Mr. Fluffikins” (coincidentally their security verification answer), but if I tell you my authenticator says “224 544” right now it does absolutely nothing to getting through MFA on my account.
Biometrics
Fingerprint readers, retina scanners, facial recognition, etc. are all forms of biometrics. Biometrics rely on inherent properties of the user. This works for and against security though. A mask can fool facial recognition, while a carefully crafted gloves can trick the fingerprint reader. Biometrics are inherent properties, so the entire method needs to be changed if they’re compromised. Collecting biometrics for work and similar also presents privacy issues for their storage and usage.
Which Method Works Best?
Most standard 2FA solutions use the principle of possession, but this doesn’t mean it’s objectively the best method. Each of these methods performs a balancing act between convenience and security. Knowledge is the easiest to get and easiest to track without extra equipment. Biometrics are the hardest to copy (at present, deep fakes and technology aren’t helping here), but they’re also impossible to (practically) change. You can’t just grow new fingerprints. Possession strikes a balance. An item or a device can be revoked, but users have to account for an extra device. If you forget your phone, you’re out of luck.
Possession is the most practical at present. Having a physical device means that stealing a one-time key or password is near useless (unless the algorithm can be cracked), and the device can be revoked if it is physically misplaced or stolen. We use the principle of possession (and a degree of knowledge for an added challenge) for ID 20/20, our in-house MFA solution. The trick is using a device someone will (almost) always have and a way to authenticate without inconveniencing the user.
Why Is MFA So Important?
Phishing and social engineering are some of the biggest security threats to businesses. MFA helps neuter phishing and social engineering attacks by adding a layer that an end user will struggle to give away. It’s easy to type your password into the wrong box, but how do you give your phone or a USB key out too? You also know almost instantly when one of these devices is missing.
You can try and train end users, but people don’t always listen and don’t always want to learn. It’s hard to tell the difference between l and I, or why it matters if a site is .com or .org. What does it mean if a certificate is invalid? Most users don’t know, and more importantly, they don’t really care. They see an email saying they have to “act now” to prevent a catastrophe and they act. Attackers prey on ignorance and emotion.
MFA throws a wrench in the gears for this. The username and password are only two of the three parts to the key. Without the third part, the whole exercise doesn’t accomplish much for its direct target. If 2FA or MFA in general is available, enable it. If a product doesn’t offer MFA and it’s going to have personal information or other sensitive data, ditch it as soon as possible.
Using More Factors
The more factors in use for authentication, the harder it is for an attacker to get in. The more important information is, the more factors which should be in play. Ideally, use multiple challenges. Have a secondary knowledge test on top of a possession based challenge. Stack the odds in your favor.
A targeted enough attack might get the username and password, but it’s harder to get MFA information. Harder, but not impossible. Your user might tell someone their mother’s maiden name or it might even get breached from a targeted attack elsewhere. The more unrelated pieces of information and unrelated challenges there are, the harder it is to actually breach an account even if the credentials are leaked. Your mother’s maiden name doesn’t help much when it’s necessary in conjunction with a one-time password.
Using MFA
MFA is often seen as a hindrance and an inconvenience, but it’s more important now than ever to use it. Apply MFA where you can to reduce the attack surface for a given product. If you are helping your client find a MFA solution, try to go with something they use already. Don’t go with Google Authenticator if they have to use AuthAnvil already if you can help it.
You don’t want your bank giving away your money to the wrong person, and you don’t want your users doing the same to their employer either. Present MFA implementation as a protection for the client’s business rather than just a plain “security measure” with cryptic “future risks”. Don’t introduce a technical solution without making it mean something to the client. If you frame MFA the right way, clients will jump on it, but frame it the wrong way and it becomes an inconvenience with no tangible benefit. Sell MFA as a good business move.
Make MFA work for your client and not against them. Even an extra password or some other knowledge based challenge is going to be better than nothing. It doesn’t have to be over the most efficient solution, it just needs to work and provide security.





