How CVE-2020-0601 the Chain of Fools / Curveball / NSACrypt Attack Affects You

by Sage Driskell
CVE-2020-0601 was announced to the public on January 14, 2020, as a warning about the Cryptographic API in Windows 10 and Server 2019 (there are rumors of Server 2016, but we have not explicitly verified this) and with a patch to resolve the issue on affected machines. As of reporting, there were no known attacks using this attack vector in the wild. Since then, the vulnerability has gotten a name (actually a few names), and some researchers have released proofs of concept.
If you want to validate a system and whether it’s susceptible or not, go to: this test.
What Is It?
CVE-2020-0601 is known by several names now. There’s Curveball and NSACrypt, as well as Chain of Fools. There are several names in circulation, but they all point to the same flaw. Let’s go over what the exploit is first.
Per Microsoft:
A spoofing vulnerability exists in the way Windows CryptoAPI (Crypt32.dll) validates Elliptic Curve Cryptography (ECC) certificates.
An attacker could exploit the vulnerability by using a spoofed code-signing certificate to sign a malicious executable, making it appear the file was from a trusted, legitimate source. The user would have no way of knowing the file was malicious, because the digital signature would appear to be from a trusted provider.
A successful exploit could also allow the attacker to conduct man-in-the-middle attacks and decrypt confidential information on user connections to the affected software.
The security update addresses the vulnerability by ensuring that Windows CryptoAPI completely validates ECC certificates.
If we dig a little deeper with newer information, we find the following from cert.org:
The Microsoft Windows CryptoAPI, which is provided by Crypt32.dll, fails to validate ECC certificates in a way that properly leverages the protections that ECC cryptography should provide. As a result, an attacker may be able to craft a certificate that appears to have the ability to be traced to a trusted root certificate authority.
Any software, including third-party non-Microsoft software, that relies on the Windows CertGetCertificateChain() function to determine if an X.509 certificate can be traced to a trusted root CA may incorrectly determine the trustworthiness of a certificate chain.
Microsoft Windows versions that support certificates with ECC keys that specify parameters are affected. This includes Windows 10 as well as Windows Server 2016 and 2019. Windows 8.1 and prior, as well as the Server 2012 R2 and prior counterparts, do not support ECC keys with parameters. For this reason, such certificates that attempt to exploit this vulnerability are inherently untrusted by older Windows versions.
So, a core function in Windows 10 based OSes for determining the key of an ECC cert which has been generated can’t be trusted until this patch is applied. This does not affect older Windows OSes though.
What Is Elliptic-Curve Cryptography (ECC)?
Elliptic-Curve Cryptography (ECC), or ECC is a form of cryptography using a mathematically generated curve algorithm instead of the traditional key method. In short, we’re passing some variables to build a key to an algorithm rather than just passing a big key to do our encryption and decryption (obviously, this is a gross simplification). This means that we use less complexity for stronger encryption (theoretically).
The basis of ECC is the following equation: y2 = x3 + ax + b
If we graph an arbitrary example of this, say: y2 = x3 – 5x + 10, we get:
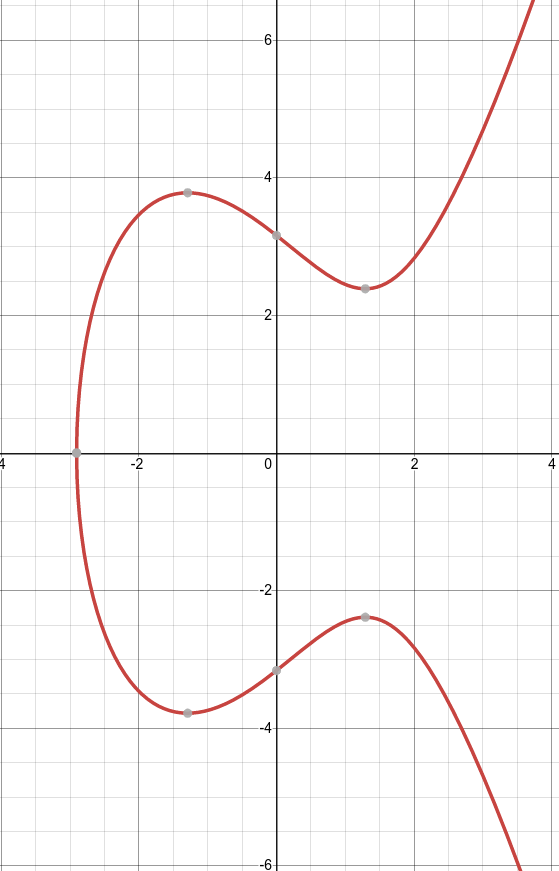
A diagram of an ECC curve for: y^2 = x^3 – 5x +10
The way the ECC algorithm works is we draw a line through parts of the curve and let it “bounce” per a known algorithm. We know it will “ricochet” a certain way and with some other conditions we can get a starting and an ending spot where it crosses the curve and bounces across. These numbers will be meaningful with a little data, but almost useless otherwise. There are a lot of equations which will get you the same algorithmic result for a few points, but if you don’t know the parameters, you don’t know the underlying pieces that make up our “key”. This means a smaller key for a harder problem for all intents and purposes.
We won’t really get any further into the math, but basically, as long as we verify all of our points and all of the variables, we’re safe.
Throwing a Curveball
The problem is, for whatever reason, Crypt32.dll doesn’t verify this correctly on certain Windows 10 and Server 2019 builds. One theory is that it’s failing to verify the base point in the equation and is assuming everything is kosher on the math checking out otherwise. Hopefully there is a bit more to this vulnerability, but either way, arbitrary ECC certificates are vulnerable without this patch on certain versions of Windows.
The issue is we’re (almost definitely) doing the math correctly, just Microsoft has decided to take a few shortcuts which compromise the validation of arbitrary ECC algorithms. See the following for a PoC.
How Bad Is It?
It’s a bit scary that something this fundamental is broken on modern Windows, but there’s some good news, it’s really not that bad with a little common sense. You won’t see this issue with Firefox since it doesn’t rely on Cryp32.dll, and other browsers like Chrome have issued patches. Most AV solutions already block the generated certificates, including Windows Defender. A good firewall which inspects SSL certificates can block this as well. Ultimately, this threat has been blocked by most end-user products, the OS, and even theoretically at the network level (transport level in TCP/IP for those of you getting your certs). This also does not impact Windows Update as those are signed using RSA.
The threat has been sold as a huge deal, and it is when used. Fortunately, the attack is non-trivial (at the time of writing) so it requires a significant degree of effort to execute, plus there is requisite setup to pull off the attack. It’s a big deal, but so is a car crash. Drive safely and you probably won’t have an issue and you prevent what you can. At present, this threat is an implementation exploit and not a cryptographic exploit.
CVE-2020-0601: Reacting to the Threat
If you have an advanced firewall which can inspect certificate chains, apply those settings if possible (some apps require certs which are superficially suspicious looking) to stop all of the man-in-the-middle attacks related to this on the internet. Your AV should update itself to stop the other attacks in most scenarios, and if not, be sure to apply the patch for this vulnerability.
This is a good time to apply more secure firewall policies at a site and agent level if possible. This is a vulnerability with the specific implementation of the cryptography and not the math behind it. As long as the cryptography itself is sound, you are too as long as you can prevent the specific implementations from being vulnerable. When you throw on an advanced firewall setting to check this, you add a different way of interpreting the math into the equation and effectively check twice using the same thing implemented differently.
If this had affected Windows 7 or Server 2008 (R2), what would happen? There’s no support and this exploit (despite being relatively harmless with some preparation) would be a much bigger deal for a company and for administrators. Windows 10 has active support, but what if your AV vendor stopped caring as well as the primary OS vendor? This is a great chance to spearhead a forced move away from legacy OSes where possible.
What’s the Difference Between Two-Factor Authentication (2FA) and Multi-Factor Authentication (MFA)?

by Sage Driskell
All Two-Factor Authentication (2FA) is Multi-Factor Authentication (MFA), but not all MFA is 2FA. Multi-Factor Authentication works on the principle of using multiple pieces of secret information in order to verify identity. Standard usernames and passwords can be brute forced, but using a separate piece (or more) of information makes this more and more impractical. Some MFA schemes will use secret questions (effectively extra passwords), or a one time key from some kind of authentication application.
MFA and 2FA are a prerequisite for security anymore. It used to take days to guess an 8 character password, now it takes literal minutes on a $35 Raspberry Pi. Everything requires a password, and people can be lazy and recycle passwords. If a user’s password is compromised for one site, who knows what other accounts are now compromised? Even the most trivial 2FA or MFA solution can reduce the impact substantially.
How Does MFA Work?
MFA (and by extension 2FA) add a protection scheme based on knowledge, possession, or biometrics.
Knowledge
This form of authentication relies on a knowledge based challenge. This can be an extra password, a security question, or some other type of challenge. The goal here is to buy time without inconveniencing the user. By adding a separate password, an attacker has to gain access to both passwords, and avoid locking themselves out trying to do so. Some challenges will have multiple potential knowledge tests to make this more complex.
Some of the first MFA I ever worked with was through a bank. The bank had a list of 20 images which you picked from and added a description to. Each time you logged in, it would give you a subset of the images, you picked the one you had, and then it prompted you for the description. If you got it wrong 3 times, it locked the account for some period of time. My password got hacked plenty of times, but my account never did. Even something this low-tech ended up stopping dozens of potential breaches.
By having you pick the specific image first, it tested your knowledge. The prompt would then pop up no matter what was picked. This method is somewhat safe, but not foolproof by any stretch of the imagination. A single incident with a keylogger could get everything.
Possession
Possession challenges rely on the physical possession of a device or some other item. This can be a USB key or a device which generates a code. Most things people think of as 2FA are generally going to be a password based on possession of an application which generates a one-time key.
Almost everyone has something like Microsoft Authenticator or Google Authenticator on their phone for work or just general security. If someone manages to compromise your computer, they don’t necessarily get your account outside of the current session. Using a separate device to authenticate mitigates the effectiveness of a keylogger or of a very coordinated attack to gather information on a target. A user can tell someone about their first pet “Mr. Fluffikins” (coincidentally their security verification answer), but if I tell you my authenticator says “224 544” right now it does absolutely nothing to getting through MFA on my account.
Biometrics
Fingerprint readers, retina scanners, facial recognition, etc. are all forms of biometrics. Biometrics rely on inherent properties of the user. This works for and against security though. A mask can fool facial recognition, while a carefully crafted gloves can trick the fingerprint reader. Biometrics are inherent properties, so the entire method needs to be changed if they’re compromised. Collecting biometrics for work and similar also presents privacy issues for their storage and usage.
Which Method Works Best?
Most standard 2FA solutions use the principle of possession, but this doesn’t mean it’s objectively the best method. Each of these methods performs a balancing act between convenience and security. Knowledge is the easiest to get and easiest to track without extra equipment. Biometrics are the hardest to copy (at present, deep fakes and technology aren’t helping here), but they’re also impossible to (practically) change. You can’t just grow new fingerprints. Possession strikes a balance. An item or a device can be revoked, but users have to account for an extra device. If you forget your phone, you’re out of luck.
Possession is the most practical at present. Having a physical device means that stealing a one-time key or password is near useless (unless the algorithm can be cracked), and the device can be revoked if it is physically misplaced or stolen. We use the principle of possession (and a degree of knowledge for an added challenge) for ID 20/20, our in-house MFA solution. The trick is using a device someone will (almost) always have and a way to authenticate without inconveniencing the user.
Why Is MFA So Important?
Phishing and social engineering are some of the biggest security threats to businesses. MFA helps neuter phishing and social engineering attacks by adding a layer that an end user will struggle to give away. It’s easy to type your password into the wrong box, but how do you give your phone or a USB key out too? You also know almost instantly when one of these devices is missing.
You can try and train end users, but people don’t always listen and don’t always want to learn. It’s hard to tell the difference between l and I, or why it matters if a site is .com or .org. What does it mean if a certificate is invalid? Most users don’t know, and more importantly, they don’t really care. They see an email saying they have to “act now” to prevent a catastrophe and they act. Attackers prey on ignorance and emotion.
MFA throws a wrench in the gears for this. The username and password are only two of the three parts to the key. Without the third part, the whole exercise doesn’t accomplish much for its direct target. If 2FA or MFA in general is available, enable it. If a product doesn’t offer MFA and it’s going to have personal information or other sensitive data, ditch it as soon as possible.
Using More Factors
The more factors in use for authentication, the harder it is for an attacker to get in. The more important information is, the more factors which should be in play. Ideally, use multiple challenges. Have a secondary knowledge test on top of a possession based challenge. Stack the odds in your favor.
A targeted enough attack might get the username and password, but it’s harder to get MFA information. Harder, but not impossible. Your user might tell someone their mother’s maiden name or it might even get breached from a targeted attack elsewhere. The more unrelated pieces of information and unrelated challenges there are, the harder it is to actually breach an account even if the credentials are leaked. Your mother’s maiden name doesn’t help much when it’s necessary in conjunction with a one-time password.
Using MFA
MFA is often seen as a hindrance and an inconvenience, but it’s more important now than ever to use it. Apply MFA where you can to reduce the attack surface for a given product. If you are helping your client find a MFA solution, try to go with something they use already. Don’t go with Google Authenticator if they have to use AuthAnvil already if you can help it.
You don’t want your bank giving away your money to the wrong person, and you don’t want your users doing the same to their employer either. Present MFA implementation as a protection for the client’s business rather than just a plain “security measure” with cryptic “future risks”. Don’t introduce a technical solution without making it mean something to the client. If you frame MFA the right way, clients will jump on it, but frame it the wrong way and it becomes an inconvenience with no tangible benefit. Sell MFA as a good business move.
Make MFA work for your client and not against them. Even an extra password or some other knowledge based challenge is going to be better than nothing. It doesn’t have to be over the most efficient solution, it just needs to work and provide security.
Creating a Mandatory Advanced Cybersecurity Package for MSP Clients
by Travis Ray, Channel Account Manager at Infogressive
If only it was that easy, right? Unfortunately, the landscape of cyber threats is evolving faster than MSPs and their clients can keep up with. MSPs know that offering a cybersecurity package is a great way to add MRR and protect their clients, but offering is the wrong approach. Advanced security services should be mandatory for all clients.
I’ve helped MSPs develop this strategy and add $15-20K of MRR immediately. Typically, less than 5% of their client base will opt out. You might lose a couple of clients, but they’re probably the clients you’ve wanted to fire anyway. Here is how to implement this strategy:
Fill gaps in your current MSS stack.
Start by looking at what you offer now and where the gaps are. Utilize a defense-in-depth approach and a security foundation like the CIS 20 Critical Controls to help identify what you have covered in your current lineup and where you fall short. In fact, there’s a free resource that allows you to take an assessment of your current security and receive a cybersecurity report card based on the CIS 20 Critical Controls.
Many MSPs’ security services are mostly preventative: Firewall, Anti-Virus, and maybe email security or security awareness training. Unfortunately, preventative security is not a guarantee that your clients will be adequately protected—you need to compliment prevention with detection. Consider services like EDR, SIEM, and Vulnerability Management. Partner with an MSSP if managing these kinds of services would be a challenge for your technical staff. By outsourcing, you add MRR with new mandatory services without the overhead and limit your liability as well.
Once you have the new services identified, begin working on a pricing structure, per seat or per user, and so on. Don’t be afraid to charge 25-40% of your current pricing model for this new security package.
Educate clients about cybersecurity.
You don’t want to spring mandatory services on clients without warning. Instead, start by developing an educational strategy. Quarterly Business Reviews (QBRs) are a great medium—if you aren’t already doing QBRs, start doing them now. QBRs will also make it easier to show the value of the new security services after they have been implemented.
Use your marketing and sales teams to start engaging clients about security and reiterate what security services you offer. Use industry-specific security statistics and start telling the story: “As your trusted advisor on IT, it’s our responsibility to make sure you know cyber-crime is a real risk to your business that needs to be mitigated.” Security education needs to be a priority for at least a full quarter.
Create your documents.
While sales and marketing are educating customers, operations and leadership should be creating the new services announcement and an opt-out agreement. Your mandatory services announcement should include pieces from your education campaign to reinforce the need, what is currently provided, what is going to be mandatory going forward (and why those services), what the cost will be, and when it goes into effect. Do NOT offer the opt-out in the announcement. The opt out is a last resort for customers who refuse to mitigate their risk.
Your opt-out agreement needs to get their attention. By opting out, the client is accepting 100% of the liability. Thoroughly outline the risks the customer is accepting. If the opt out agreement will not make the client pause and reconsider, it’s not strong enough. Include projected costs of responding to a cyber security incident for a client of their size and industry, along with additional costs to deliver managed services while the client is breached, even if they do not use your firm for incident response.
Launch your new Mandatory Cybersecurity Services.
There are two ways to launch your new Mandatory Cybersecurity Package:
- In phases to your entire customer base:
This is the approach I recommend to my MSP partners. Start with a portion of your smaller customers to make future phases easier and learn from unforeseen challenges. Now you are better prepared for phase two and three, minimizing challenges for those more critical clients. Phases two and three will be comprised of fewer customers but more endpoints and ensure it’s not overwhelming for your technical team.
- At renewal of existing managed services:
This strategy can be easier from contractual and deployment standpoints, putting less strain on operations or engineering teams. However, you lose negotiation leverage with clients that push back since they might have already been shopping other providers with their renewal coming up.
In summary…
If you are not protecting your clients with an advanced cybersecurity package, you’ll probably lose them as a client when (not if) they suffer a cybersecurity incident. An advanced mandatory security package shows your value as their trusted IT advisor and adds coveted MRR for you, the MSP. If a customer elects to opt out, your liability is minimal and potential loss of a client has less impact after substantially increasing MRR from the 95%+ of your clients that accepted.
About the author
Travis Ray is a Channel Account Manager at Infogressive, a Master MSSP established 2006 in Lincoln, NE. Prior to joining Infogressive, Travis has worked in the channel with MSPs and helped dozens of partners build security go-to-market strategies. Travis is an award-winning channel sales professional and worked the sales cycle from beginning to end as a dedicated resource for his partners, earning praise and recommendations on LinkedIn from partners, colleagues, and leadership.
Infogressive is a Managed Security Services Provider (MSSP) that has combined the best technology available with passionate cybersecurity experts. They take pride in partnering with MSPs to provide the security they and their clients need in this ever-changing threat landscape. Infogressive knows the ins and outs of what is needed to stay secure from the bad guys, which is proven by their history of zero data breaches since their beginning in 2006.
The Danger of Free Proprietary Software
If you Google “free software” right now, you’ll get two definitions. One is free, open-source software (FOSS), and the other is freeware. The two are dangerously different though.
FOSS is a community endeavor for better software, but can lack in some of the refinement brought by the financial advantages of proprietary software. For a lot of enterprise environments and MSPs, FOSS probably won’t be ideal (compliance headaches, support, etc.). Freeware has no real barrier to entry and no real oversight. Not all freeware is bad, but you have to tread carefully.
With the news of the AVG and Avast plugin in the news lately, it’s hard to trust even the bigger freemium software distributors. Data theft is just the tip of the iceberg though. Freeware has had PUA’s (Potentially Unwanted Applications) embedded to make money, and some even include spyware and other malware. You have the Internet of Things which has no real updates or transparency. There is also the threat of cryptojacking which has made its way into websites and applications.
Data Theft
The AVG and Avast plugin issue came to a head due to data theft. Both companies are betraying their customer’s trust in order to make a quick buck by harvesting and reselling their data. This is nothing new, but it is especially worrying for a freemium model security solution. What else is doing this?
The answer is probably a disgusting number of software suites. Many free software suites have to make money, and data harvesting is one of the cheapest, easiest, lowest impact methods to do that. What separates this data theft from spyware? Basic semantics.
PUPs and PUAs
Aside from harvesting data, you also run the risk of them including extra pieces in the form of Potentially Unwanted Programs (PUPs) and Potentially Unwated Applications (PUAs). Both are the exact same, but different security suites name them differently.
A lot of sites with free downloads may repackage an application to include trash like the ask.com toolbar or similar. They make money either by offering this as an option or by each successful install. These potentially unwanted installs can lead to security issues. Sometimes it pays to just spend a few dollars to find a solution which only includes what it needs.
The Internet of Things
The Internet of Things (IoT) is a perfect example of these issues in one package. The IoT can be viewed as selling a device which includes free software. It can also be viewed as a huge security risk and privacy risk.
If the device isn’t profitable, neither is the proprietary software. And once the software doesn’t make money, well… it’s gone and dead. Your expensive smart device is now a really expensive paperweight. Some of them can’t even work as dumb devices when the main servers go under. The Internet of Things is no stranger to being a security concern for you and your business.
Cryptojacking
Cryptojacking is used to describe when a website or an application takes over a computer to mine for cryptocurrency for a threat actor. Any application that packages cryptomining may as well be the same exact thing though. Again, the only difference is in asking permission buried in an unreadable blog of legalese and asking forgiveness if actually caught.
Some free software products or sites package in cryptocurrency mining software which can create instability and serves as a general security issue. This type of violation can also affect productivity as this proprietary software often impacts the machine’s performance. As the gains from cryptocurrency get more and more promising, this type of monetization scheme will only get more and more common.
Why It Happens
FOSS has an ideal behind it, to create free, open-source software and to make sure that the software stays free. This comes at the cost of not being beholden to the market and potentially lacking features or the impetus to push ahead. ClamAV is free, but it doesn’t really win any awards for efficiency.
Proprietary software follows a philosophy more in line with making money. Software is given away for free to either build a reputation, or to serve as a loss leader. If a company isn’t big, why are they giving you the software for free? Treat it similarly to how you do phishing.
Some small companies may give it away for free because they want to (like Nirsoft), but many do it to work towards a goal. What is the end goal? If you don’t know, then why are you using it?
Stopping the Security Concerns
Make sure antivirus and other security tools are deployed across any site you manage. Use Group Policy in domain environments to lock down installations to control the environment. The harder it is for a user to install an application, the harder it will be for a user to accidentally install malware. Block sites which contribute to these sorts of things.
We use Kaseya in conjunction with OpenDNS and Huntress for response. Kaseya’s RMM portion, VSA, can alert on program installation. For tightly controlled environments, this is ideal. For more lax environments, this can be overkill and more noise than it’s worth.
OpenDNS assists by blocking common spam and phishing sites which can use legitimate programs as a way to slip in adware and similar. You won’t have stopped AVG or Avira this way, but you stop some of the more sinister pieces of software. Huntress can help for response to the more questionable types as well.
Ultimately, the only way to really stay on top of this for your client is to perform regular audits. Collect audit data from the site and comb over it for anything out of place. The sooner you see anything out of place, the sooner you can act on it before the site is compromised.
Adding Value
Security audits take a lot of work, but there are plenty of ways to help automate these processes. This can be an easy upsell to the client. How much does your time cost and how much does the service cost? How much does it save them paying you to audit the service for them? Done right, this means you can charge a retainer to review things while they get assurance everything is good if they get hit with a massive bad installation. The bill is the same each month, and you get money each month.
This is also a chance to either sell a commercial product which might have volume licensing for cheaper than list price, or a chance to sell a support contract to open source software (think Nagios). It depends on your strengths, what you do with your company, and what your client does which is going to be the best fit. If you sell a commercial antivirus, what about response and similar? Software is software, make it a package and make it more profitable if you can. It can also be worth outsourcing SOC services with a minimum guarantee.
Similar applies to open source software you sell a support contract for. Having a technical point of contact at the site can be worth a good amount. You are the IT professional, you should be the professional onsite. You control the environment and make sure the customer doesn’t get taken for a ride or waste time. This is win-win for both parties.
Stopping Dangerous Free Proprietary Software
While free open software isn’t right for everyone and doesn’t fit most businesses, it also tends to be more honest compared to freeware software. Know which one is right for your client and show your value as their IT concierge. With all of the different attacks from data theft to cryptojacking, you have to protect your clients from their tools and from themselves.
Use monitoring solutions and response tools to prevent and contain bad proprietary software. Use GPO and similar administrative tricks to minimize unintended and unsupervised installations where possible. Control devices in the environment and prevent things from creeping (e.g. flat networks). If you play your cards right, this becomes a value add and a new upsell rather than an inconvenience. The magic is in adding value, the more value you add for the client, the more you add for yourself in the longevity of the contract.

by Sage Driskell
SaaS, IaaS, XaaS: The Commoditization of Tech as a Service
SaaS, or Software as a Service, is the most well-known of the transition from traditional tech offerings to service offerings. This move turned a single fixed cost into a recurring payment and raised the overall cost per client while reducing the perceived impact for the client. SaaS grew into PaaS and IaaS and then finally into the general concept of XaaS, Anything as a Service. The floodgates were open for commoditizing various elements of the tech industry.
SaaS: Software as a Service
The reduction in cost for high speed internet, especially in business centers, has pushed software providers away from traditional per-seat licensing modeling towards SaaS. SaaS is attractive to both service providers and end users by offloading the cost of maintaining a traditional server stack or workstations to a vendor, got end users constant updates without having to pay for upgrades, and allowed providers to control the stack and milk recurring payments out of the arrangement. The overall cost over the lifetime of a client goes up substantially, but the perceived cost to the user goes down.
SaaS made it so all the user has to worry about is using the software. It also takes away some degree of control over the environment. This loss of control led to the commoditization of even higher levels of abstraction which give various amounts of control back to the end user.
IaaS: Infrastructure as a Service
Infrastructure as a Service, or IaaS, gives the ultimate control back to the end user. IaaS takes the guesswork out of provisioning hardware and makes the entire virtualization process transparent. You pay for the resources you use, speed of the network or disk, and basically nothing else. You can spin up entire domains with advanced routing this way.
Vendors like US Signal, Microsoft, and Amazon all have these as offerings. These types of offerings completely offset initial costs for spinning up a cloud environment however you want. IaaS does require significant upkeep on the user side for anything running in the environment.
PaaS, the Middle Ground: Platform as a Service
PaaS, or Platform as a Service, is last since it’s the hardest to nail down of the three. It exists somewhere between SaaS and IaaS and is basically defined in practice by being an offering with more control than SaaS, but without the full maintenance or control of IaaS. You basically control the platform, but not the implementation.
PaaS offerings sit somewhere between SaaS and IaaS, but usually drift closer to one or the other. A lot of SaaS providers will have a PaaS offering as well for added extensibility. IaaS vendors may have a PaaS offering which is a simplified version of their primary infrastructure.
Basically, PaaS means you support most of the application, but shouldn’t have to worry about the operating system or backend. A lot of PaaS providers will provide various additions and other things to make a lot of that not a worry though. It is a wildcard term for everything in between SaaS and IaaS in practice, so your expected responsibilities may vary. This is something to clear before signing a contract.
XaaS: Anything as a Service
SaaS, PaaS, and IaaS laid the groundwork for all sorts of services from small scale to large. Any part of maintaining a traditional business from a technical side has become fair game with XaaS, which is Anything as a Service. XaaS is the embodiment of commoditization of anything in the technical industry. Everything from network setups as NaaS (Network as a Service) to backup and disaster recovery as DRaaS (Disaster Recovery as a Service) or BDR (Backup and Disaster Recovery) exist now.
Integrating XaaS Into Your Business
We covered the basics of what each of SaaS, PaaS, IaaS, and XaaS are. These are some great terms, but what do they actually mean for a business? For an MSP, these are an upsell. You offload the maintenance of an onsite product to the cloud and bill for it. For your clients, you reduce risk and upfront costs by offloading a painful setup to a cloud environment with easier access and lower yearly costs compared to all of the other costs added together.
Like the move from block time to truly managed services, once everything is set up, you basically print money to be on call if something unexpected breaks. Be a good janitor for tech; your clients should never know you’re there, but they should know what would happen if you were gone. Your work should be a quiet black box they rarely see unless something unexpected pops up or a user has issues with something they’re doing. What is the client going to want to see, a report on what you’ve done that has prevented issues, or more stuff broken being fixed? The hardest part of servicing a client in a managed scenario should be in the beginning.
For businesses, XaaS offers a higher Total Operating Cost, but it normalizes unexpected costs almost entirely. Most services end up cheaper than maintaining the amortized cost of a server, the power and internet required to make it work, and the cost of the software license(s). The power of scale cuts the costs and makes the service more powerful. Not every option is right though depending on business requirements.
Finding What Is Right For Your Clients and Yourself
With all the options, it can be hard to shop. Where do you draw the line between SaaS and PaaS, or PaaS and IaaS? The lines blur badly with many options. It doesn’t help that each vendor has their own arbitrary distinction between service levels. PaaS may be IaaS for some features, and little better than SaaS for others.
Weigh the client’s resilience to change, their budget, and their want for flexibility. The more SaaS you get, the fewer options you have for customization. The more towards IaaS you get, the more resources are required to integrate the environment and make everything work. Sometimes flexibility comes at the cost of consistency, and other times flexibility is what makes consistency possible.
You need to ask yourself and your client why you’re moving to the cloud in the first place. Is it to cut costs or is it to offset responsibility? Is it for remote access without opening up their network or is it for easy updates? There are many reasons to move, all of them equally valid to a business. You have to understand the why to plan the how.
Commoditizing Technology as a Service
Most techs feel a bit dirty being a middle-man for a cloud offering. After all, you’re not really doing the lifting for the service and you’re getting money for it. While this holds true if you aren’t adding value to the process, what is your expertise, research, and ability to make sure everything works worth?
The old story about a plumber goes: a client calls a plumber and the plumber fixes his issues within a minute and bills the client $1,000. The owner throws a fit and demands an itemized bill to justify the bill since all he did is turn a spigot. The plumber gives him a bill which has two items on it, “turning the spigot, $1, knowing which spigot to turn, $999”.
Filtering the results for the client, helping them get started, and making sure everything integrates and continues to integrate smoothly is worth a lot to a nontechnical client. Don’t shortchange yourself if you can make their experience worth the bill markup.
With the business move to XaaS, your consolidation of options into a package provides value to the client and presents an opportunity to reduce fail points and improve reliability. The cloud isn’t infallible, but you take hardware maintenance, software maintenance, etc. out of the equation for you and your clients. It can cost more, but you reduce the work involved in making everything work together for both you and especially your client.
Avoiding the Security Pitfalls of the Cloud
Cloud offerings and XaaS have made it trivial to offload almost any given part of a business from the backend to the workstations. There are serverless environments and even cloud workspaces which are agnostic to what technology your end users are using. These can all present security issues when not thoroughly vetted and integrated properly.
It’s easy to fall for the trap of setting up a flat network to make everything work. Flat network topologies are insecure since everything can talk to everything else (among other reasons). The use of basic routing to divide the network up helps slow down many attacks. There is a maintenance cost and a technical cost to implement this however. This can be another upsale though. Either bake it into the pricing as a feature of your service or add it on.
Application
Knowing the difference between all of the different types of cloud services can help you better understand which is right for you and your business. Each offers its own range of features and has its own set of limitations. Sometimes the limitations are features for certain people. You have to know the use case to fully assess which option is truly best.
SaaS was the catalyst, but technical services are commoditized and the options can leave you dazed. Knowing what works with what and how to implement various offerings as a holistic ecosystem can be a major value add to clients. Security is extremely important as well and cannot be forgotten for the sake of convenience.

by Sage Driskell
ID 20/20: Putting a Stop to Social Engineering
2019 marked the first year a deepfake was used to pull off a heist. 2020 is likely going to be the last year it makes it to the front page though. The cat’s out of the bag with this one.
There’s a lot to be concerned about for 2020. Windows 7 is reaching end of life, the Internet of Things is everywhere, and everything is more connected than ever before. There are so many security concerns, but most of them can be fixed by applying basic security principles and technology.
The one thing that technology has so far been unable to change is the threat of social engineering. As Kevin Mitnick put it in his keynote at VISION 2019, social engineering is the easiest way to get into any given network. It doesn’t matter how smart the system is if the person behind it is stupid and unlocks it for them.
There are solutions, but most of them are cumbersome for IT administration. Things like Duo require installation of an app or some other end user interaction. We thought about this and built a system called ID 20/20 targeted with ease for end-users in mind. Your bank doesn’t make you install an app to call in, so why should any other service? Let’s go over what makes social engineering tick and what makes ID 20/20 so different from other security solutions.
What Is Social Engineering?
At its highest level, social engineering is the use of human weakness to exploit a network. This is where someone calls in and pretends to be “Carl from the accounting department” and is locked out of the building or his account with the hopes the person answering doesn’t check. This gets especially problematic in larger companies where it is harder to know who someone is. Social engineering preys on common, social courtesy.
Social engineering is made even more problematic when it is combined with technology. There are tools to steal RFID card codes, compromised personal information on the dark web, and countless ways to ascertain information in the digital age. It’s near trivial to spoof a phone number with the right tricks. There are deepfake programs which can emulate a voice live.
How Could Social Engineering Impact an MSP?
How soon do you know about a fired employee from one of your clients? How often do you take inventory of employees at a given company? These all seem like a waste of time at first, but if you know who can ask for what from your client, you can prevent compromises and reduce costs.
A fired employee may call the help desk before they’re notified and ask for a trivial account to be made which can later be used to shred files. Whose fault is that one? Will your client just happily accept it wasn’t yours and be on their way? Almost definitely not, and even if they do, a single employee can bring down a business with the right damage.
By keeping tabs on your clients, you further understand what different people do which can help you better tailor your services and get acquainted with potential opportunities for upsales. It gives you a stronger relationship and keeps your client safer. You also lower the chance of social engineering because you know who is who at the company and you make sure when someone is fired, you know first. You also know if “Carl from accounting” is actually someone there.
How Could Social Engineering Impact The 20?
To put it simply, The 20 takes the MSP model and extrapolates it to the next level. Multiple clients could be hit without the right preparation against social engineering. We know this and we take security seriously.
Due to the fact that we have so much oversight into so many environments, we need to be sure we know who we’re talking to has permission to do what they’re asking for. It doesn’t matter if they claim to be the regional VP if they aren’t documented properly (though obviously we say this a lot less directly to the client). What happens when an MSP’s employee is terminated and calls in for a password? We tell them the same thing, no. We have to, or else we’d be compromised. Process needs to be followed or else social engineering becomes trivial.
What is ID 20/20?
In the era of deepfakes, we had no choice but to evolve with the times, so we created ID 20/20. ID 20/20 is a multi-factor authentication solution which takes out any requirement from the end user except they have an email address or a cell phone (and either one can be optional if necessary), and even a code for places where they can’t be near a computer or phone.
We thought through the pain points of our end users so that they are safe but not impacted. We also thought through the pain points of our partners and what makes it hard to push out these kinds of changes. Applying security changes is always hard, but it doesn’t have to always be painful.
How Does ID 20/20 Stop Social Engineering?
ID 20/20 requires a user verify their identity partially verbally then again with a randomly generated code which is sent to their email or cell phone. The tech then asks them for this code and puts it into the system which verifies. The tech does not know the code and does not volunteer any information about the user unless necessary. This prevents us from unwittingly providing information to a potential malicious actor.
ID 20/20 sits on top of the standard operating procedure of the site as well. By combining these factors, we limit what a user can get from us and what they can do unless they’re authorized. The process takes about a minute total so far.
It also integrates with Kaseya BMS in order to update a ticket to log what the tech did, whether they were successful or not, and helps keep track of how the client was verified. If a client won’t cooperate, you know. If someone has been unable to be verified, you know. There are no more questions of whether a tech followed protocol or not for verification. If a malicious actor can get through, you’re already compromised.
How Can You Stop Social Engineering?
ID 20/20 can reduce a lot of social engineering attacks, but you have to also train the end users. Do you click on an email from a bank you don’t use? I know I don’t, but I know plenty of users do. Teach your users how to recognize and avoid phishing attempts.
Following a process which butts against social norms is hard, especially for things like doors. Social engineers will use door holding to get physical access. How do you tell your employees: “Pull the door shut and make the next person badge in?” It’s hard, but necessary in bigger companies. You also have to make sure verification processes are followed. There may be a “Jim in accounting,” but how do you know you have permission to grant their request or not? There has to be process.
Conclusion
Technology may eliminate as many issues with security as it helps create, but little has previously been manageable with social engineering. Social engineering preys on common courtesy and the fallibility of the human element. ID 20/20 aims to address that weakness with the cold resolve of a machine for the underlying process and a human face guiding the process to make it acceptably warm.
ID 20/20 is ready to address the technological side of many social engineering attacks with negligible overhead for the end-users. Just because deepfakes are here, doesn’t mean they will get through unchecked. We thought ahead, what about you?

by Sage Driskell



